How Open Source Can Help Protect Your Organization Against Email Threats

Email is one of the most prominent methods of modern business communication. It is a critical dissemination channel for sharing legal documents and other confidential business information in any formal environment. However, email is also the root cause of over 90% of all attacks in network security, such as phishing, URL spoofing, malicious attachments, trojans, and malware.
Hackers design these messages to look harmless, but a successful attack can cause severe, lasting damage, including data loss, reputational harm, and financial damage to your organization. The impact of data and cloud security breaches can be devastating for a company. Therefore, it is essential to take precautions to help your organization thwart email threats and use reputable open-source network security toolkits to secure business email.
This article will explore why the collaborative, transparent, open-source development model is superior to engineering flexible and adequate email protection. It will also offer other tips and practices Linux users should implement to ensure their data and network security within their email.
What Are Common & Costly Email Threats Organizations Face?
Email is a primary form of communication but, as a result, has become a target for cybercriminals seeking to take advantage of cybersecurity vulnerabilities. Organizations face various email threats that can lead to significant financial losses, reputation damage, and cloud security breaches. Companies should understand what they are facing to protect sensitive information and avoid network security threats.
Phishing

Phishing attacks are among the most popular and damaging network security threats for email. A cybercriminal poses as a legitimate entity, such as a bank, government agency, or well-known brand. They then use this identity to deceive recipients and obtain sensitive information that can allow them to breach data and network security. Phishing emails often contain persuasive messages that urge recipients to click on malicious links, provide login credentials, or disclose confidential data.
It is important to decipher between typical phishing and spear phishing. While phishing targets many users, a spear attack targets a particular person, such as a company CEO. This distinction shows who faces the network security threat the most in a given attack.
There can be severe consequences for financial fraud, data loss, and cloud security breaches. The business's personal information, financial data, or login credentials could be compromised, and such knowledge could allow more attacks on network security, such as installing malware or gaining unauthorized access to an organization's network.
Ransomware
Malicious actors will use software to encrypt a victim’s data until a ransom is paid. A business can face operational disruptions, financial losses, and reputational damage due to these attacks on network security.
Ransomware emails are often disguised as legitimate messages. When one opens an attachment or clicks on a link, the ransomware is activated, rapidly encrypting files and rendering them unusable. In some cases, it can also spread throughout the organization's network, infecting multiple systems.
Remember: ransomware recovery is often problematic. Therefore, learning to prevent email threats is incredibly valuable so you never have to deal with the consequences.
Business Email Compromise (BEC)

Business Email Compromise (BEC) attacks specifically targeted organizations and their employees. Cybercriminals gain unauthorized access to an employee's or a high-ranking executive's email address. They then use these compromised accounts to deceive employees into performing fraudulent actions. Business Email Compromise includes manipulations to make people transfer money or disclose sensitive information. These attacks in network security involve a threat actor studying an organization and monitoring email communications so they can send more convincing messages during a network security threat.
A company needs a multi-layered approach to address these network security issues. This approach combines technological solutions, employee education, and robust security practices. Open-source software provides cost-effective and customizable network security toolkits to detect and mitigate these risks, enhancing overall data and network security.
Why Should My Organization Prioritize Email Data and Network Security?
Email security is vital for all companies. Here is why:
- Email is a primary means of communication for sharing sensitive information and conducting important business transactions. This makes email communications an easy access point for cybercriminals to initiate attacks on network security.
- Phishing, ransomware, and other network security threats are constantly growing in sophistication, making them even more substantial risks to organizations, regardless of the size.
- Data and network security regulations and industry standards require strict email security measures to ensure sensitive information confidentiality, integrity, and availability.
Open Source Utilization in Email Security
Organizations can enhance email security by implementing open-source software into their system, which is a community-driven approach to software development. Workers can review and improve the solutions observed by developers who keep track of cybersecurity vulnerabilities so they can fix them immediately. Open-source software can be customized and tailored to the needs of the organization.
This dedication to data and network security makes open-source software more reliable and secure, minimizing the risk of bugs and other exploits in cybersecurity.
Email Security Tips & Best Practices for Linux Users
Although Linux is more secure than other operating systems, users must still implement email security measures to defend the system and combat any data and network security threats. Here are a few suggestions to consider to protect the integrity of your company:
Use End-To-End Encryption (E2EE)
Only the intended recipient of an email can decrypt and read the message when using End-to-End Encryption. This protects the email should it be intercepted, as it will be unreadable to malicious hackers without the correct decryption key, protecting your emails from any network security threats. The intended recipient will get the email and use the private key they have to access the content in the message.
The sender and the recipient must have compatible encryption software and exchange public encryption keys securely for E2EE to work appropriately and effectively. You can check our practical guide to using E2EE on Linux for more information.
Leverage VPN
Using Virtual Private Network offers several email security benefits. VPN has privacy-enhancing technology and monitors internet traffic like email communications to ensure that all your information is encrypted and safe. As a result, hackers and unauthorized entities cannot easily access or intercept information.
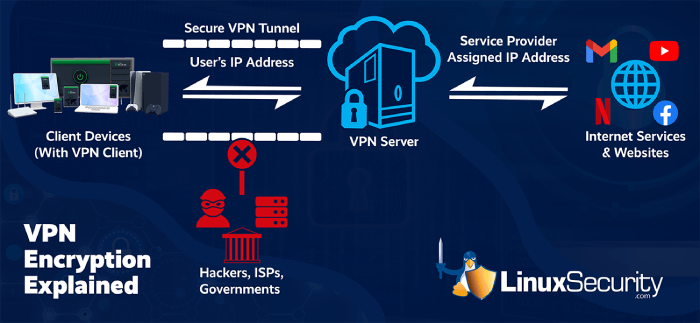
While VPN can enhance email protection and data and network security, it should be used with other safety measures such as End-to-End Encryption, secure email clients, and robust authentication methods.
Deploy an Open-Source Email Security Solution
Open-source solutions offer transparency and flexibility so you can customize data and network security configurations according to your needs. Collaboration on such products often includes regular updates, security audits, and improvements driven by a dedicated community. An open-source cloud email security solution allows users to inspect the underlying code for security measures.
Utilize Anti-Spoofing Technology
Spoofing is a network security threat that occurs when an intruder impersonates a legitimate sender to gain unauthorized access to sensitive information. To prevent these exploits in cybersecurity, Linux users can implement anti-spoofing software or technologies such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC).
SPF verifies the sender's IP address against a list of authorized ones, ensuring that only legitimate senders can successfully deliver emails. DKIM adds a digital signature to email messages for the recipient to verify the message's authenticity and integrity. DMARC builds upon SPF and DKIM to reduce the risk of domain spoofing, providing a comprehensive framework to authenticate and monitor email domains.
Ensure client software is patched and up-to-date
Developers constantly release security patching and updates to fix flaws and improve security postures, performance, and stability within a software. Updating email clients and their associated software allows Linux users to experience a more seamless integration of newer hardware components.
A business must frequently utilize security patching and software updates, which are critical to ensuring no cybersecurity vulnerabilities that threat actors can exploit. Enabling automatic updates or setting up regular reminders to manually update email client software guarantees that the latest cybersecurity trends are implemented promptly and appropriately.
To keep track of newly emerging network security threats, Linux users can check security advisories. There are databases within that discuss the various network security issues different software run the risk of experiencing. This information is available publicly and allows businesses to jump into action when a potential threat appears quickly.
Use Securely Developed Software
When choosing an email security solution, options with safe development practices are essential. Your choice should include software that undergoes regular security audits, follows secure coding guidelines, and has a responsive developer community.
Security software developers often try to reduce the risk of cybersecurity vulnerabilities and ensure that potential network security issues are identified and addressed quickly. Software choices provide customers confidence in the product, as they can be sure it has undergone rigorous security checks. Therefore, it can help reduce the likelihood of email-based security incidents and protect sensitive information.
Educate Users
Software users within an organization must be educated about the various email threats a company faces to prevent such workers from being cybersecurity vulnerabilities. Such people end up being the most significant risk to a company. Still, these free educational tips and resources will enable the users to identify and respond effectively to suspicious emails.
The training may cover topics including recognizing phishing attempts, avoiding clicking on suspicious links, preventing downloads for attachments from unknown sources, and practicing good password hygiene. Furthermore, users should understand the importance of regular email security assessments, frequent software updates, strong passwords, and enabling two-factor authentication for email accounts, all of which can guarantee improved data and network security.
Limit Administrator Privileges
There should not be a large number of users that have administrative access within your organization, as it will reduce the potential damages you risk by providing privileged permissions to too many individuals. This decreases the chances of privilege escalation attacks and other email-based security incidents.
Granting administrator privileges only to authorized personnel minimizes undesired access, accidental misconfigurations, or intentional misuse of email systems. Linux users should ensure that individuals have the level of access required to perform their specific tasks only, no more.
Implement Innovative Email Security Technologies
 To stay ahead of evolving network security threats, embrace innovative email security technologies. These solutions use cutting-edge techniques to detect and mitigate real-time email attacks. Some of the best open-source network security toolkits you can utilize in innovation include Apache SpamAssassin, Amavis Email Content Filter, FuGlu Mail Content Scanner.
To stay ahead of evolving network security threats, embrace innovative email security technologies. These solutions use cutting-edge techniques to detect and mitigate real-time email attacks. Some of the best open-source network security toolkits you can utilize in innovation include Apache SpamAssassin, Amavis Email Content Filter, FuGlu Mail Content Scanner.
These instruments provide valuable email security benefits such as effective spam detection, malware prevention, virus protection, content filtering, phishing prevention, and customization options. As open-source solutions with active communities, they offer continuous updates and improvements, ensuring robust protection against all email threats.
Other technologies can enhance email security in different ways. Virtual security patching helps protect against known cybersecurity vulnerabilities by providing temporary fixes until permanent patches are applied. Application control enables organizations to restrict the execution of unauthorized or potentially malicious software. Log inspection allows for analyzing email server logs, helping to detect and investigate suspicious activities or potential cloud security breaches.
Advanced security technologies employ Machine Learning (ML) algorithms and behavioral analysis to identify and block malicious emails. Using ML in data and network security helps prevent phishing attempts, malware infections, and other email threats. Moreover, ML-based email filtering enhances spam detection accuracy by continuously adapting to new spamming techniques, which reduces the risk of users falling victim to fraudulent emails or unsolicited messages.
Defend Against Email Threats with Guardian Digital Open-Source Email Security Solutions
Guardian Digital protects businesses against new and known email threats with its comprehensive EnGarde Cloud Email Security solution. Guardian Digital anticipates the network security threats specific to your users so workers can stop the attacks using flexible filters that adapt to your environment. EnGarde uniquely draws on network security toolkits, resources, and intelligence available through its vibrant, global open-source community to enhance protection against all email-borne threats to your business. A product of open-source development, EnGarde is supported by an innovative, collaborative international input program, resulting in rapid updates and superior security and resiliency.
Final Thoughts on Protecting Against Email Threats with Open Source
Email is a vital communication channel for all businesses, but it can also present serious network security issues if email protection is not implemented. Utilizing reputable open-source technology and implementing other tips and practices discussed in this article are excellent ways to improve the security posture of your email to defend against cyberattacks in network security and other cloud security breaches.





















