Which Browser is Best for Online Security?

Today, one of the most popular ways for free websites and browsers to make a profit is tracking and selling user data to advertisers. While most tracking is behind the scenes and discreet, allowing oneself to be tracked can have negative consequences–attackers often attempt to track users the same way legitimate companies do in order to steal data; not to mention the growing concern of companies using data purchased from legitimate sources to manipulate users.
While it may seem futile to even try to stay private on an internet dominated by companies who have a motivation to make sure their users aren’t private, there are many popular and simple ways to maintain privacy online. One of the easiest ways to maintain privacy online is to download a secure and private browser. Because the browser is the interface to the internet, a good browser can make the biggest difference when it comes to protecting your data. The Tor browser is famous for offering complete anonymity, or the closest thing possible, on the internet. However, there are many other great browsers with a focus on security without some of the flaws of Tor.
Browser Comparison Summary
|
Tor |
Firefox |
Chrome |
Chromium |
Brave |
|
|
Open Source |
✔ |
✔ |
X |
✔ |
✔ |
|
Encrypts Traffic |
✔ |
X |
X |
X |
X |
|
Can block third party/tracking cookies |
✔ |
✔ |
✔ |
✔ |
✔ |
|
Doesn’t track browsing data |
✔ |
✔ |
X |
✔ |
✔ |
|
Has a built in password manager |
X |
✔ |
✔ |
✔ |
✔ |
|
Built-in adblock |
X Tor recommends that you don’t install extensions, including adblockers |
X |
*Can “block ads on sites that show intrusive or misleading ads” |
*Same as Chrome |
✔ |
Introduction to Tor
In the 1990s, the United States Naval Research Laboratory created the theory of “onion routing” as a way to anonymize internet traffic. By 2004, it was integrated into a publicly available open-source browser known as Tor. Tor is one of the most well-known ways to browse the internet privately. Tor works by using onion routing, a process in which a user’s internet traffic is routed through several layers of a network relay, like the layers of an onion. By encrypting traffic and passing it through several servers, hackers, or even the owners of these servers, are unable to spy on the data passing through the network–only the user and the destination can read the data.
Another popular feature of Tor is its ability to access the dark web. The dark web refers to websites that can not be found with a search engine or accessed through a regular internet browser. This includes websites with “.onion” domains, which can only be accessed through the Tor browser.
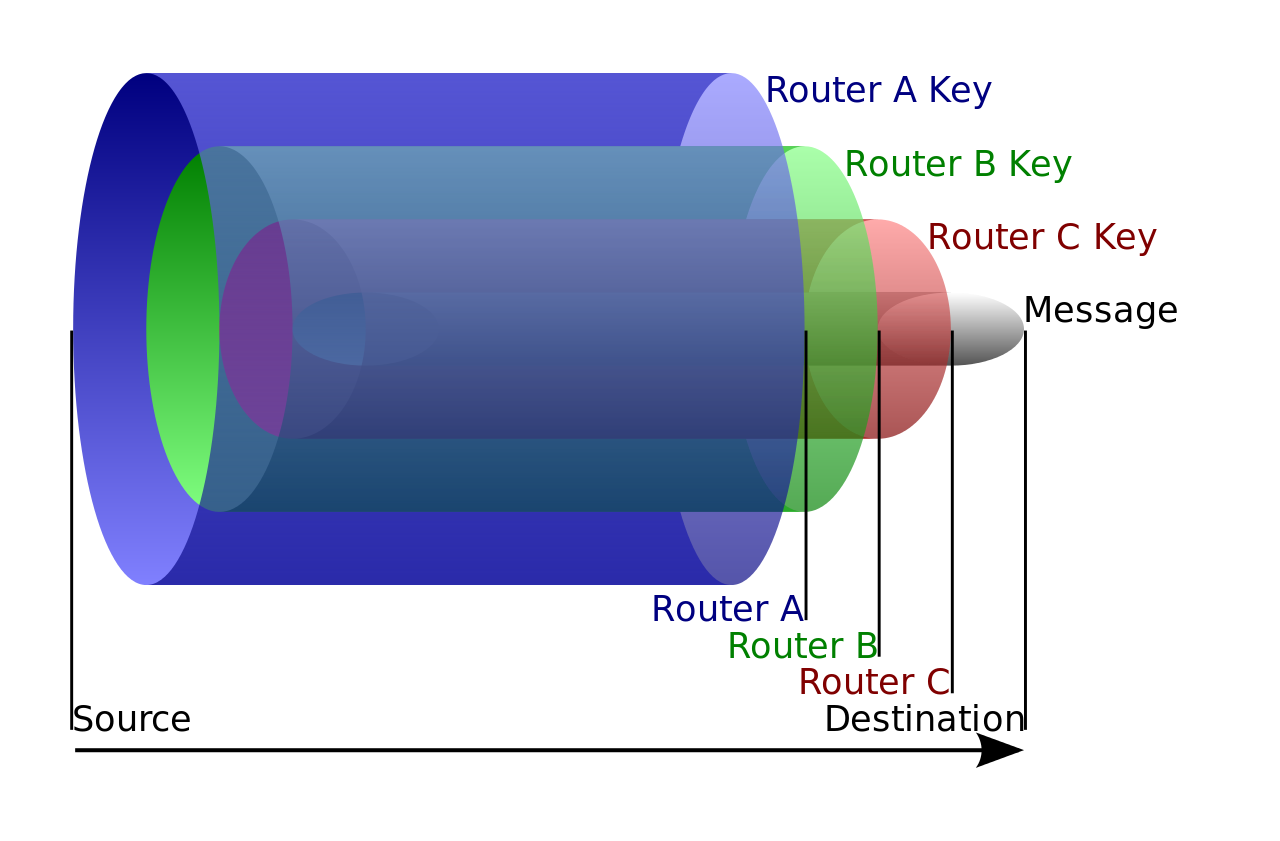 Although Tor is often seen as the gold standard for private browsing, it does have some flaws that are often overlooked. First, Tor is slower and uses more bandwidth than other browsers due to the fact that it reroutes traffic through several additional servers. Additionally, Tor recommends against using browser extensions for security reasons, which limits customizability and personalization. Users also sacrifice some benefits of other browsers, such as personalized content from cookies, due to Tor’s security measures. While many see these as a small price to pay for increased privacy, it is important to note that Tor lacks some convenient features that are seen as standard in most browsers today.
Although Tor is often seen as the gold standard for private browsing, it does have some flaws that are often overlooked. First, Tor is slower and uses more bandwidth than other browsers due to the fact that it reroutes traffic through several additional servers. Additionally, Tor recommends against using browser extensions for security reasons, which limits customizability and personalization. Users also sacrifice some benefits of other browsers, such as personalized content from cookies, due to Tor’s security measures. While many see these as a small price to pay for increased privacy, it is important to note that Tor lacks some convenient features that are seen as standard in most browsers today.
Additionally, although it sounds counterintuitive, using Tor can actually make users stand out. Like mentioned before, Tor is often used for browsing sites on the nearly uncensored dark web, many of which contain illegal content. This, combined with the fact that users going out of their way to hide their IP addresses can look suspicious, has led to many sites blocking all users with an IP address from the Tor network.
It is also important to note that Tor is still open to malware and viruses just like any other browser—using Tor does not protect users from falling for phishing scams or downloading trojan viruses. Similarly, Tor can not prevent websites from requiring accounts. If a user creates a Facebook account with his real name, phone number, and email, he is not really any more private or secure just because he is using Tor.
Finally, the onion routing methodology is not flawless. As mentioned before, websites can block traffic coming from the IP address of a Tor exit node, limiting the functionality of many sites—for example, Wikipedia can not be edited from Tor. Furthermore, since Tor relay servers are run by anonymous volunteers, users have to place their trust in other users. Over the past few years, a security researcher known as Nusenu has discovered that a growing fraction, now over a quarter, of Tor servers are run by the same anonymous user. Since the security of onion routing relies on routing traffic through several distinct layers of obfuscation, one user controlling all the layers means that he could potentially see through the curtain and decode the traffic of anyone whose traffic jumps through his servers.
Additionally, Tor is vulnerable to what is known as an “end-to-end timing attack”— if an attacker monitors both a user and the website he is attempting to access, he can use patterns, such as packet transmission time, to match traffic to a user, allowing him to deanonymize the data and what the user is doing. While these are extreme cases not likely to affect most people using Tor, it is still important to note that if someone wants to track a Tor user, it can be done.
Mozilla Firefox
 Because of all of the limits of Tor, it is not seen as necessary for the average user, especially since there are so many other secure and private browsers available. One popular browser is Mozilla Firefox, an open-source browser with a focus on privacy. Unlike Tor, Firefox is a more standard browser with features such as personalized content and browser extensions that do not compromise its security. Firefox can block cryptominers, disable certain unwanted and intrusive website features, and send do not track requests. Additionally, Firefox can block non-essential tracking cookies that are used to spy on users.
Because of all of the limits of Tor, it is not seen as necessary for the average user, especially since there are so many other secure and private browsers available. One popular browser is Mozilla Firefox, an open-source browser with a focus on privacy. Unlike Tor, Firefox is a more standard browser with features such as personalized content and browser extensions that do not compromise its security. Firefox can block cryptominers, disable certain unwanted and intrusive website features, and send do not track requests. Additionally, Firefox can block non-essential tracking cookies that are used to spy on users.
However, while Firefox is known for being a private browser, it will always inherently be less private than Tor since it does not use onion routing or provide access to dark web sites. Firefox is a good middle ground for users who want a browser with a focus on security and privacy but do not need, or do not want the compromises of, something as extreme as Tor.
Google Chrome
 Another browser with great security is Google Chrome. Chrome is the most popular internet browser, encompassing over 50% of internet usage. However, it has a well-known privacy flaw: its users are tracked by Google. Although some of Chrome’s tracking can be disabled, much of it can not be turned off. Unlike Mozilla, which blocks tracking cookies by default, Google has a motivation to allow these cookies to stay: Google’s business model relies on selling targeted advertisements, which they accomplish through their use of cookies and data collection. According to a test conducted by the Washington Post, Google Chrome stores over 11,000 more tracking cookies than Firefox in a single week.
Another browser with great security is Google Chrome. Chrome is the most popular internet browser, encompassing over 50% of internet usage. However, it has a well-known privacy flaw: its users are tracked by Google. Although some of Chrome’s tracking can be disabled, much of it can not be turned off. Unlike Mozilla, which blocks tracking cookies by default, Google has a motivation to allow these cookies to stay: Google’s business model relies on selling targeted advertisements, which they accomplish through their use of cookies and data collection. According to a test conducted by the Washington Post, Google Chrome stores over 11,000 more tracking cookies than Firefox in a single week.
While Chrome is a weak choice for privacy, it does have great security—it is the proprietary browser and one of the major products of the second largest technology company on the planet. It also has great security features, such as a built-in password manager, automatic flagging of unsafe browser extensions, a safety check that warns if a user is using a compromised password, and automatic, frequent security updates.
Chromium Based Browsers
Chromium
 Although Chrome is not the best browser for privacy, it has several offshoots that are worth considering. When Google released Chrome in 2008, they also announced that they would be releasing the entire source code as part of the Chromium project. Since then, Chrome and Chromium have diverged—Google now uses the Chromium browser as a testing ground for Chrome, then updates Chrome by taking stable features from Chromium and adding proprietary features exclusive to Chrome.
Although Chrome is not the best browser for privacy, it has several offshoots that are worth considering. When Google released Chrome in 2008, they also announced that they would be releasing the entire source code as part of the Chromium project. Since then, Chrome and Chromium have diverged—Google now uses the Chromium browser as a testing ground for Chrome, then updates Chrome by taking stable features from Chromium and adding proprietary features exclusive to Chrome.
Unlike Chrome, Chromium does not track its users, making it a good alternative to Chrome for users who want more privacy. However, Chromium does come with some disadvantages—first off, it does not have automatic updates like Chrome, leaving it open to security vulnerabilities if a user forgets to manually update. Additionally, it can be confusing to install—while Chrome is meant to be easy to install, with a huge “Download Chrome” button on its site and a setup program, the raw version of Chromium is mostly meant for developers and can be more difficult to find and install. Additionally, since Chromium is used to test new features, it is generally less stable than Chrome.
Brave
 Ultimately, while Chromium has privacy benefits over Chrome, it is less stable and must be manually updated, leaving it open to security vulnerabilities. However, since Chromium is open-source, there are many different browsers built using its code. One popular Chromium-based browser is Brave. Brave is a browser based on Chromium that is developed with privacy in mind. Brave automatically blocks both ads and third-party tracking cookies, is open-source, and does not track users. Additionally, since Brave is built on top of Chromium, it is compatible with regular Chrome extensions. Brave also has a unique feature—it allows users to open private windows that send their traffic through the Tor network, essentially giving users the anonymity of Tor with the functionality of a regular browser.
Ultimately, while Chromium has privacy benefits over Chrome, it is less stable and must be manually updated, leaving it open to security vulnerabilities. However, since Chromium is open-source, there are many different browsers built using its code. One popular Chromium-based browser is Brave. Brave is a browser based on Chromium that is developed with privacy in mind. Brave automatically blocks both ads and third-party tracking cookies, is open-source, and does not track users. Additionally, since Brave is built on top of Chromium, it is compatible with regular Chrome extensions. Brave also has a unique feature—it allows users to open private windows that send their traffic through the Tor network, essentially giving users the anonymity of Tor with the functionality of a regular browser.
While Brave is one of the best browser options for privacy, it does have some flaws. First, its Tor windows do not offer the full privacy and security of Tor—they just send traffic through the Tor servers. Additionally, Brave has had some controversies in the past, such as when users found that the browser automatically and secretly redirected users to Brave’s referral links when they try to sign up for certain cryptocurrency websites. However, Brave is still one of the best browsers for privacy and its flaws are relatively minor compared to its security benefits.
Additional Resources for Staying Private
In addition to using a privacy-oriented browser, there are other ways to make browsing the internet more private. Virtual private networks, or VPNS, are software that encrypt and reroute internet traffic through a server. This allows users to hide their browsing activities from third parties, such as internet service providers and hackers. Browser extensions like ad blockers can also make browsing the internet more private and secure. Ad blockers hide advertisements, which can prevent intrusive and dangerous ads, and disable unnecessary tracking cookies.
Conclusion
While Tor has many features that average browsers can not compete with, its flaws can weigh it down for the average user. Users who will benefit most from Tor are people who are actively being tracked, such as militaries and people who know they are being spied on. For most users, a secure and private browser like Firefox, Brave, or even default Chromium, should be enough to stay safe, especially with safe browsing practices and software like VPNs or adblockers.
Ultimately, even though many of the biggest websites and technology companies rely on collecting user data, it is not impossible to stay private and secure online. Secure browsers, such as Tor, Firefox, and Brave, can significantly improve internet security by default, and adding a VPN or adblock is more than enough for the average user to stay secure online.




















