What Is the Impact of AI on Cybersecurity? 3 Interesting Use Cases

Thank you to Lerma for contributing this article.
What is the impact of AI on cybersecurity today?
AI is making a difference for companies feeling the pinch of strained resources. The resilience of tech-savvy cyber hackers is another reason cybersecurity strategists are quickly adopting artificial intelligence-powered solutions.
With the increased pace and complexity of digital attacks, analysts can make do with limited manpower, and keep at bay cyber threats no matter the size of company operations.
Small to large businesses are tapping into AI tools to find vital threat data from an ocean of countless news reports, forums, and research papers.
These data-driven AI analytics tools are then enabling cybersecurity professionals to choose suitable protection measures.
More specifically, various industries are using AI-powered cybersecurity strategies to:
- Prevent malware attacks
- Ensure network safety against DNS threats
- And protect employees from social engineering schemes.
In this article, we’ll be discussing these 3 cybersecurity use cases to uncover the impact of artificial intelligence on cybersecurity.
Let’s get started.
1. Social Engineering Protection
Social engineering may come in many shapes and forms in today’s digital climate.
A phishing attack is always lurking around the corner.
Sometimes, a weird-looking email pops up on your company’s account, as a bad actor tries to impersonate one of the partnered brands in an information-swindling attempt.
Clicking on one of the links leads to a fishy website or platform containing mimicking login portals to key in sensitive information about clients or the business.
The major problem with these types of attacks is that it can be so HARD to separate what’s genuine from what’s not.
Artificial intelligence through deep learning tools can be the shield that protects your business from such phishing attacks and other forms of social engineering.
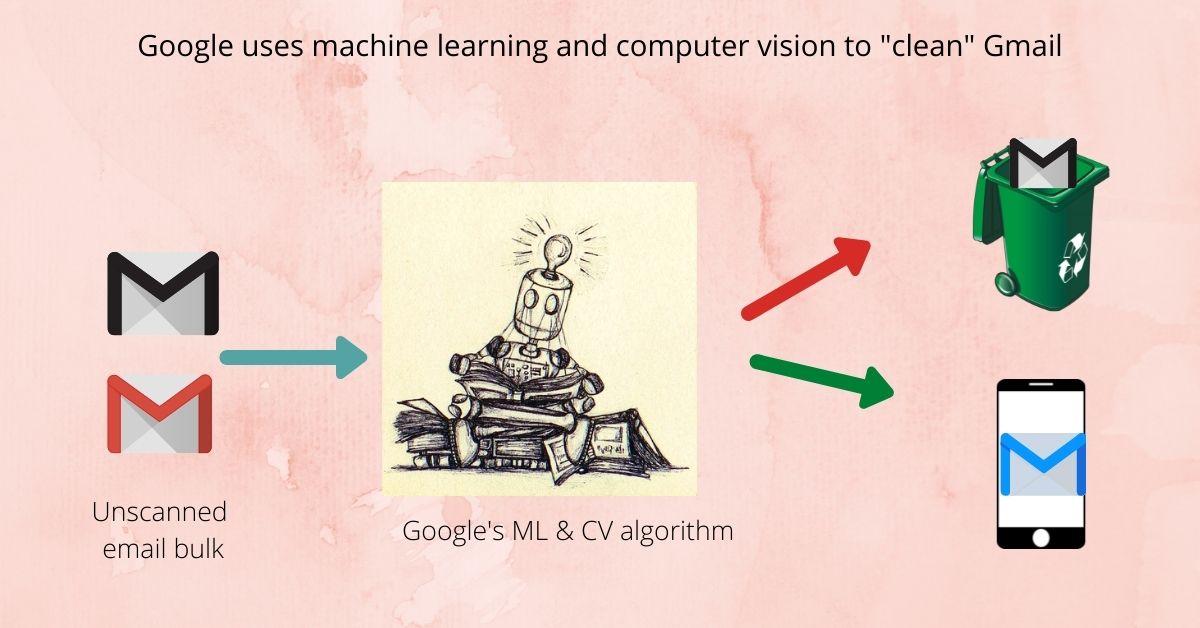
Google is already using deep learning to protect its Gmail users from phishing attempts in the same manner.
The search engine giant uses a combination of deep learning and computer vision to screen billions of image-based emails, like you’d do in a big data analytics project, and then quarantine possible threats.
Deep learning is a more comprehensive take on machine learning, where an AI “brain” learns to solve difficulties on its own. Unlike basic machine learning, where algorithms learn only from labeled data, deep learning takes in large quantities of statistics.
A deep neural network forms and evolves beyond examples to deal with new threats, unfamiliar to the system. So even if your business faces a new threat that the system hasn’t learned from yet, the algorithm should still be able to offer protection.
If you were to receive spam or phishing emails, the DL neural network would block these emails from even getting into your company networks.
The criteria for social engineering blocking may be flagging down newly created domain messages and suspicious hard-to-read emails, among other metrics that cybersecurity analysts can finetune according to your company needs.
2. DNS Threat Detection
Is it possible to spot a Domain Name System (DNS) attack and prevent it before damage is done?
DNS is essentially the internet’s directory. When we look up some of our favorite websites, we key in phrases or domain names such as espn.com, or google.com.
A DNS translates these website names into a language that devices can understand and work with, namely IP addresses. In a nutshell, the DNS enables movements between websites.
Your company may be vulnerable to a DNS security threat in one of two ways. There are various ways of preventing a DDoS attack before it actually happens.
The first is a Denial of Service attack. In a DoS threat, your DNS server is overloaded with so much traffic that it cannot attend to legitimate queries from real clients.
The second type of DNS threat is an amplification attack. What happens here is that your client is directed to a knock-off version of the business website. Despite typing in the correct address, the compromise in the DNS means your clients land elsewhere and type in sensitive login details into this deceptive website.
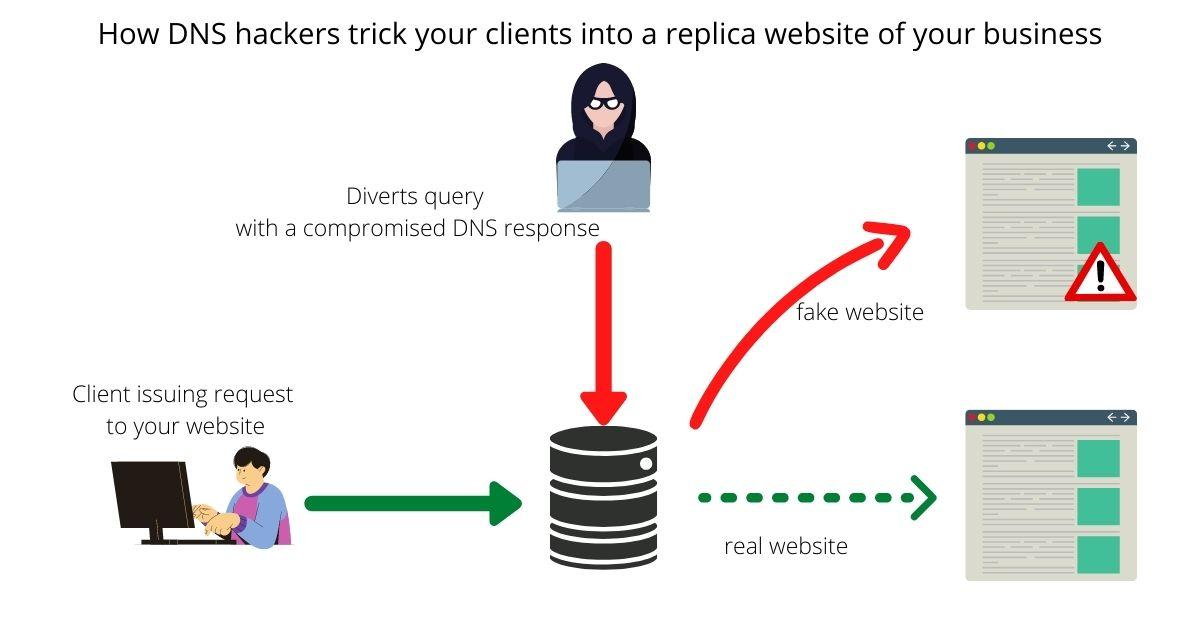
Businesses can solve DNS cyber attacks such as these by using an AI-powered network for threat identification.
This network monitors all the traffic flow in and out of DNS servers. Afterward, it separates legitimate website user requests from malicious ones, aimed at tricking business systems into amplification or DoS attacks.
Financial institutions, an industry prevalent to DNS threats, are putting AI-driven DNS solutions to work with software that entails a database of previous cyber threats, and crosschecks all the DNS traffic against a checklist of what an attack would look like.
If the software notices data anomalies that might be an attempt at a DNS maneuver, it brings this to the attention of human staff.
Human workers can then take corrective action, e.g. by denying the request or actually calling up the client in the case of a pending transaction.
3. AI-driven Malware Identification
 What type of antivirus software do you rely on to stay on top of your cybersecurity needs? Is this choice of antivirus software in line with the cybersecurity trends of the day?
What type of antivirus software do you rely on to stay on top of your cybersecurity needs? Is this choice of antivirus software in line with the cybersecurity trends of the day?
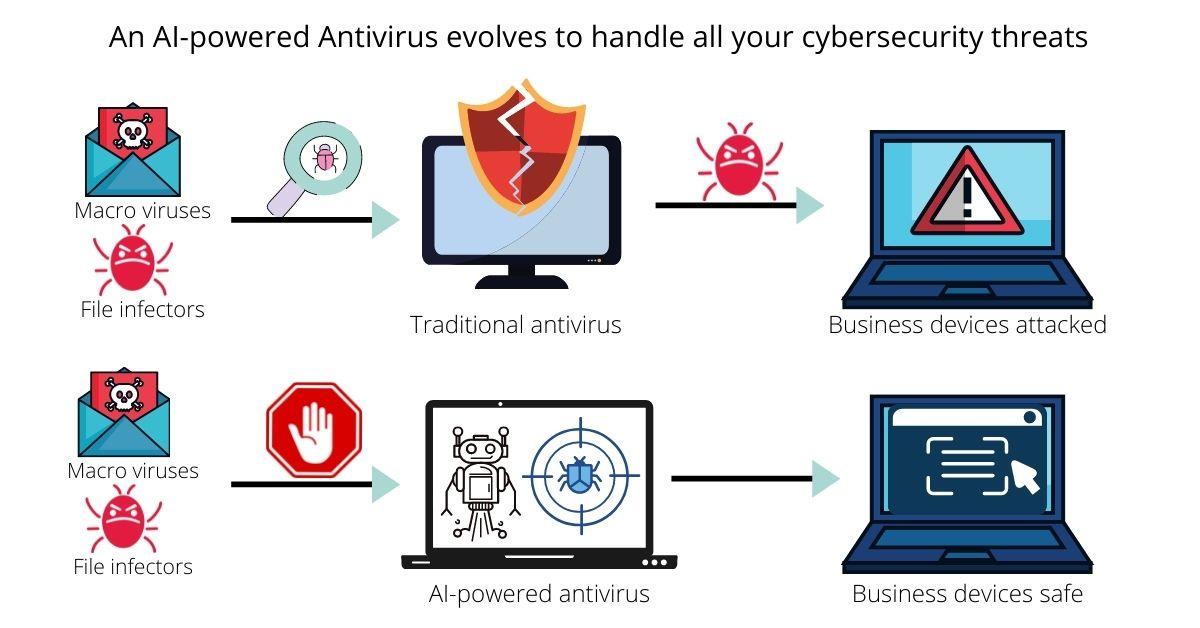
I’ll take a wild guess and say that it’s probably not AI-powered. Relying on traditional antivirus packages, means limited protection as these are programmed to protect companies from known threats.
While traditional antiviruses may get the job done for a while, the problem is that there’s a window of vulnerability to threats outside the range of familiarity.
In other words, the antivirus is programmed to protect against certain specific cyberattack malware only. Hence, it won’t be of much help in cases where businesses are up against new malware signatures, which may go unperceived as a threat.
For example, if the antivirus is conditioned for polymorphic and macro viruses, it will come up short when dealing with file and boot-record infectors.
An AI-powered antivirus software, on the other hand, protects your business from both cyber attack malware known to it, and emerging ones.
Instead of relying on a comparison metric to identify threats, an AI-driven antivirus runs on an anomaly detection system. This new antivirus, therefore, doesn’t sync to known malware signatures, instead monitors individual programs to see which one puts a foot wrong.
So if say some type of malware has hijacked one of your workplace programs, like MS office, the AI-powered antivirus will take note of the app’s unusual behavior. The program will then be singled out for a scan, and the threat is excavated from hiding and eliminated.
Just like the AI powered email security solution by Guardian Digital, software gurus Cylance unveiled a smart antivirus project that works similarly.
The antivirus detects threats via a mathematical machine learning algorithm, which becomes adept at singling out threats over time.
It doesn’t need regular updates to stay informed of new threats that have cropped up since the previous update. Instead, Cylance learns from scratch and experiences, thereby getting better with time at executing protection duties.
Conclusion
Are current AI trends and principles part of your cybersecurity strategy?
There are many benefits in store with AI-powered defense measures, including adaptability to new threats and better detection and response times.
Relying only on traditional strategies of digital security is like bringing a knife to a gunfight. Cybercriminals are leveraging modern-day technology to easily get the upper hand over outdated security models, and no business should get left behind.
By incorporating AI into protection systems, you can keep up with the pace of the digital war and stand up successfully against cyber threats of the future. The company will remain safe and also avoid possible legal trouble with clients.
Therefore, consider artificial intelligence solutions in cybersecurity like AI-powered antivirus software, DNS-threat detecting networks, and social engineering AI shields.
About the Author
Lerma is a cyber security analyst and technical writer with experience in network security, penetration testing, and artificial intelligence. Some of his favorite tools are Metasploit, the Burp Suite and Kali Linux of course.




















