Open Source Vulnerability Assessment Tools & Scanners

Computer systems, software, applications, and other interfaces are vulnerable to network security threats. Failure to find these cybersecurity vulnerabilities can lead to the downfall of a company. Therefore, businesses must utilize vulnerability scanners regularly within their systems and servers to identify existing loopholes and weaknesses that can be resolved through security patching.
Assessment results help developers and network administrators understand any potential network security issues so they can implement the necessary defensive measures against them. In this article, we will discuss what vulnerability scanners are and introduce our top free, adaptable, open-source vulnerability assessment tools.
What is a Vulnerability Scanner?

A vulnerability scanner assesses the network security issues in a system or application. Scanners automate website and cloud security auditing to improve security posture by checking your website for network security threats.
Vulnerability scanners can also list prioritized cybersecurity vulnerabilities you should patch. This list describes the type of vulnerability and the necessary steps to fix it. Some vulnerability tools even have automated security patching.
It’s crucial to patch any problems swiftly because they can put a system at a higher risk of cyberattacks. These network security threats let hackers enter your system and utilize exploits in cybersecurity to their advantage, potentially causing an immense loss for your business.
Vulnerability scanning tools rely on vulnerability databases to automatically test for known risks. Like fail2ban or antivirus software, these vulnerability scanners are crucial in maintaining maximum data and network security for your website.
Types of Vulnerability Scanners
Four broad categories classify vulnerability scanners:
Data-based vulnerability scanners
In today’s digital world, storing critical organizational data has burdened databases heavily. Losing such information can result in reputational damage and monetary losses.
Data-based vulnerability scanners search for cybersecurity vulnerabilities within databases, such as missing patches, weak passwords, and misconfigurations. These vulnerability testing tools also highlight weaknesses in real-time to notify users so they can immediately mitigate network security issues.
Network-based vulnerability scanners
Seamless and constant connectivity within the network dramatically increases the risk of data and network security compromise, hence the existence of network-based vulnerability scanners.
These vulnerability scanner tools identify weaknesses within the network and look out for possible attacks in network security through both wired and wireless systems in real time.
Host-based vulnerability scanners
Even though web hosting has various security measures embedded into the platform, this service can still have some weak spots.
Host-based vulnerability scanners can be installed on every host within a system to provide in-depth insight into potential cybersecurity vulnerabilities and network security issues coming from insiders or outsiders who have partial access.
Cloud-based vulnerability scanners
The increased dependency on cloud security solutions, especially during the evolving remote work lifestyle, has contributed to the tremendous demand for cloud-based vulnerability scanners. These vulnerability testing tools primarily scan and detect possible network security issues to websites and other online assets within a business.
Our Top Vulnerability Scanning Tools
Many vulnerability scanners are available online that you can purchase, obtain for free, or use as an open-source tool. When looking for vulnerability scanning tools, you should focus on finding one with the reliability, industry reputation, unique features, ease of setup and use, and scalability options your company needs. Here are a variety of free, open-source vulnerability scanners to keep in mind when making your decision.
Aircrack-NG Open Source Vulnerability Scanner

Aircrack-ng is a highly regarded open-source vulnerability scanner that detects wifi and wireless cybersecurity vulnerabilities. Its main benefits include speed, accuracy, and flexibility, making Aircrack-ng a valuable online vulnerability scanning tool for security professionals.
Here are Aircrack-ng’s key benefits:
- Ability to detect web application security vulnerabilities in wifi networks and devices
- Support for a wide range of wireless hardware and protocols.
- Comprehensive coverage of wireless network security issues, including WEP and WPA-PSK cracking.
- User-friendly interface with extensive documentation and tutorials.
- Integration with other network security toolkits and cloud security frameworks.
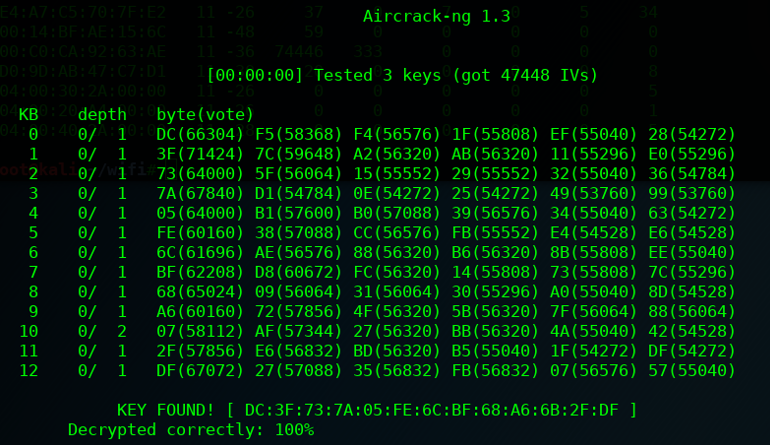 Aircrack-ng has advanced algorithms and techniques for detecting wireless cybersecurity vulnerabilities and can perform active and passive scanning. Its modular architecture allows for easy customization and integration with other security tools, making it a versatile and valuable online vulnerability scanning asset for security professionals. The tool's specialized focus on wifi and wireless vulnerabilities makes it well-suited for wireless network testing and security patching.
Aircrack-ng has advanced algorithms and techniques for detecting wireless cybersecurity vulnerabilities and can perform active and passive scanning. Its modular architecture allows for easy customization and integration with other security tools, making it a versatile and valuable online vulnerability scanning asset for security professionals. The tool's specialized focus on wifi and wireless vulnerabilities makes it well-suited for wireless network testing and security patching.
Anchore Open Source Vulnerability Scanner
Anchore is an open-source Docker container policy compliance and static analysis tool. Anchore automatically scans container content image, analyzes, and evaluates upon activation. The result provides a policy evaluation for each image and determines whether it passes or fails a business’s requirements to be one of its vulnerability scanner tools.
Anchore analyzes the contents of the container image to discover hidden cybersecurity vulnerabilities. Its vulnerability database will assist in scanning for known web application security vulnerabilities to ensure that the container image follows the best security standards and industry practices. Most importantly, Anchore integrates with container registry and CI/CD tools.
Anchore is an open-source vulnerability scanner designed to help organizations identify and manage cybersecurity vulnerabilities in their containerized environments. It is particularly well-suited for use in DevOps and containerized environments, where applications are deployed in containers and continuously monitored for data and network security issues.
Here are Anchore’s key features:
- Automatically scans container images for known network security threats and provides detailed reports on the vulnerabilities found.
- Provides detailed information on the contents of container images, including software packages and dependencies, which can help you identify potential security risks.
- Allows you to define and enforce custom policies to ensure that only trusted and secure images are used in your environment.
- Integrates into your CI/CD pipelines to automatically scan container images for cybersecurity vulnerabilities before deployment, helping you catch network security issues early in development.
Overall, Anchore is one of many powerful vulnerability scanning tools that can help you identify and manage web application security vulnerabilities in your containerized environments and ensure that your applications are deployed securely and reliably.
Arachni Open Source Vulnerability Scanner
Arachni is a highly regarded open-source vulnerability scanner that detects web application security vulnerabilities. Its main  benefits include speed, accuracy, and flexibility, which make it a valuable online vulnerability scanning tool for security professionals.
benefits include speed, accuracy, and flexibility, which make it a valuable online vulnerability scanning tool for security professionals.
Here are the Arachni’s key benefits:
- Comprehensive coverage of web cybersecurity vulnerabilities, including SQL injection, cross-site scripting, and directory traversal.
- Ability to scan both static and dynamic content.
- Customizable scanning options and reports.
- Integration with other network security toolkits and cloud security frameworks.
- User-friendly interface with extensive documentation and tutorials.
Arachni has advanced scanning engines that use a combination of heuristics and signatures to identify web application security vulnerabilities. Its modular architecture allows easy customization and integration with other network security toolkits, making it a versatile and valuable asset for security professionals. The tool's specialized focus on web network security issues makes it well-suited as one of various web application vulnerability testing tools.
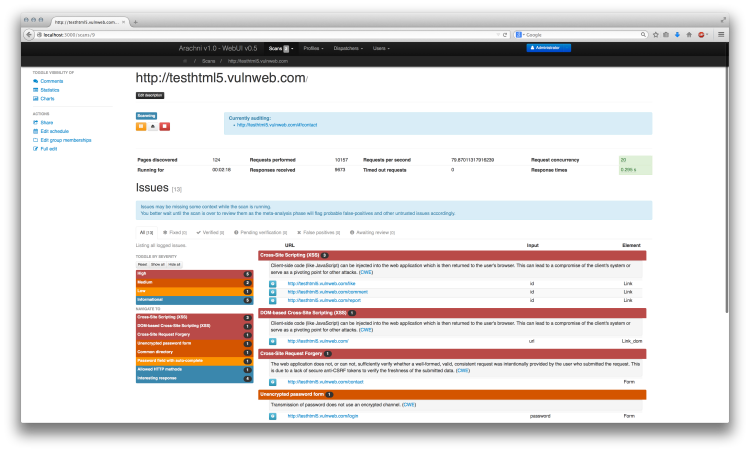 Burp Suite Free Edition Open Source Vulnerability Scanner
Burp Suite Free Edition Open Source Vulnerability Scanner
 Burp Suite Free Edition is an open-source vulnerability scanner and comprehensive network security toolkit that checks for web application security testing through scanning, intercepting, and modifying HTTP requests and analyzing responses.
Burp Suite Free Edition is an open-source vulnerability scanner and comprehensive network security toolkit that checks for web application security testing through scanning, intercepting, and modifying HTTP requests and analyzing responses.
Here are Burp Suite Free Edition’s benefits:
- Support for multiple operating systems and platforms.
- Powerful scanning capabilities for web applications.
- Ability to identify various web application security vulnerabilities, including SQL injection and Cross-Site Scripting.
- User-friendly interface with extensive documentation and tutorials.
- Integration with other network security toolkits and cloud security frameworks.
Burp Suite Free Edition has extensive features, making it a one-stop shop for web application vulnerability testing tools. Its ability to intercept and modify HTTP requests allows complex web applications and APIs to be tested. Additionally, the tool's open-source nature allows for community contributions and customizations.
Clair Open Source Vulnerability Scanner
Clair is an API-based vulnerability scanner that lets you check for known cybersecurity vulnerabilities in each open-source container layer. These vulnerability management tools create a monitoring service that keeps an eye out for web application security vulnerabilities. Clair regularly collects vulnerability metadata from various sources, indexes container images, and provides an API where you can retrieve picture features. This network security toolkit can also alert you whenever the vulnerability metadata is updated, allowing you to find new cybersecurity vulnerabilities from previously scanned images.
Clair also provides an API that you can use to query network security issues in specific container images. Its main benefits include its speed, accuracy, and scalability, making Clair a valuable tool for security professionals. Here are Clair’s key benefits:
- Comprehensive coverage of container images and their associated vulnerabilities.
- Support for a wide range of container image formats and registries.
- Easy integration with container orchestration systems like Kubernetes and Docker Swarm.
- User-friendly interface with detailed vulnerability reports.
- Ability to scan containers in real time.
Clair focuses on containerized environments and provides detailed vulnerability reports for container images. While it is not explicitly designed to detect wifi and wireless cybersecurity vulnerabilities, Clair effectively identifies network security threats that could be exploited through containerized or wireless attacks.
Lynis Open Source Host Vulnerability Scanner
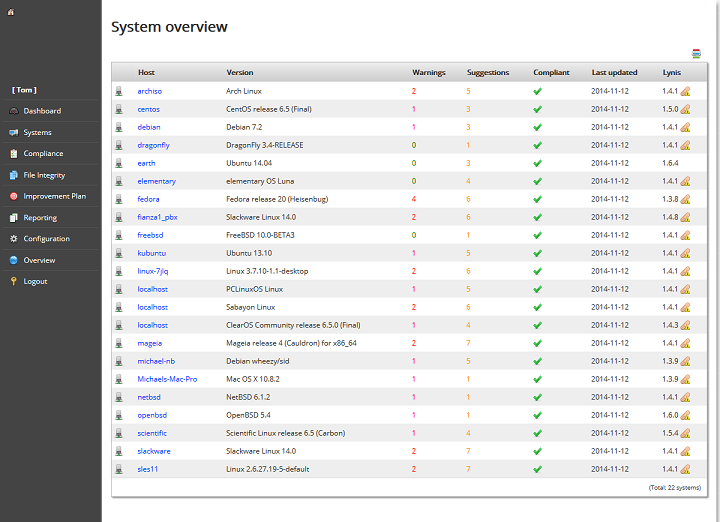
Lynis is an open-source host-based vulnerability scanner that can identify network security threats in Linux and UNIX-based systems. It is designed to be lightweight, easy to use, and highly customizable, allowing users to tailor the online vulnerability scanning process to their needs.
Here are Lynis’ key features:
- Identifies a wide range of cybersecurity vulnerabilities and misconfigurations in a host, including network security issues with file permissions, system settings, and services.
- It is designed to be user-friendly due to the clear and concise output that highlights potential exploits in cybersecurity and provides guidance on how to fix them.
- Customize Lynis to specific needs, tailoring the scanning process to focus on particular areas of concern or to exclude certain checks.
- It is free and open-source, so anyone can use and modify it freely, and the source code is available for review and audit.
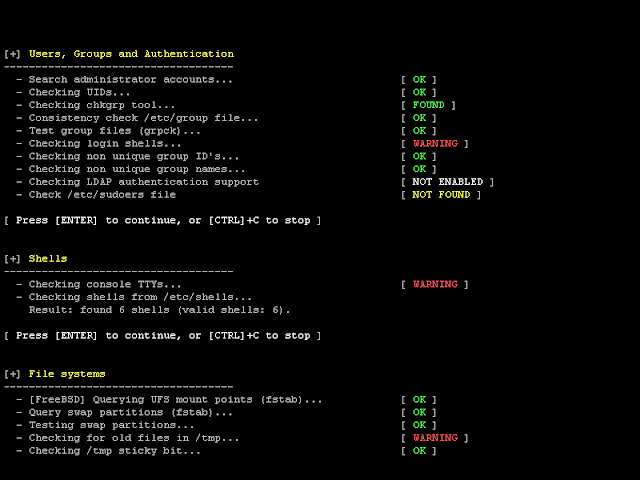 Lynis can be a valuable network security toolkit for organizations looking to improve security posture in their Linux and UNIX-based systems, providing a comprehensive and customizable way to identify and remediate cybersecurity vulnerabilities.
Lynis can be a valuable network security toolkit for organizations looking to improve security posture in their Linux and UNIX-based systems, providing a comprehensive and customizable way to identify and remediate cybersecurity vulnerabilities.
Metasploit Open Source Vulnerability Scanner and Framework
Metasploit is a penetration testing cloud security framework that can identify exploits in cybersecu rity within computer systems and networks.
rity within computer systems and networks.
Metasploit can detect:
- Remote code execution vulnerabilities
- SQL injection vulnerabilities
- Cross-site scripting (XSS) vulnerabilities
- Directory traversal vulnerabilities
- Buffer overflow vulnerabilities
- Authentication bypass vulnerabilities
- File inclusion vulnerabilities
- Misconfigured services and applications
In addition to detecting vulnerabilities, Metasploit can also simulate attacks in network security and attempt to exploit identified cybersecurity vulnerabilities. This allows security professionals to test the effectiveness of their security controls and evaluate the potential impact of actual attacks on network security. Metasploit also has an extensive library of exploit modules and payloads, making it a valuable tool for security professionals and ethical hackers.
Nmap Open Source Vulnerability Scanner
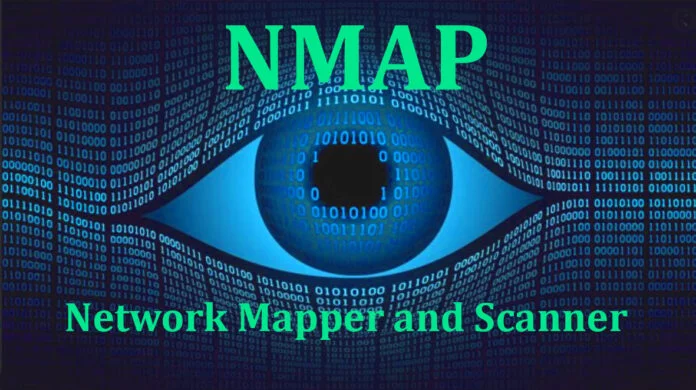 Nmap is a popular open-source vulnerability scanner widely used in the data and network security community. It allows users to discover hosts and services on a network, identify potential cybersecurity vulnerabilities, and perform various tasks related to privacy sandboxing and security patching.
Nmap is a popular open-source vulnerability scanner widely used in the data and network security community. It allows users to discover hosts and services on a network, identify potential cybersecurity vulnerabilities, and perform various tasks related to privacy sandboxing and security patching.
Here are Nmap’s key benefits:
- Ability to perform rapid and accurate scanning.
- Can detect various types of vulnerabilities.
- Provides detailed information about target/ed systems.
Nmap is highly regarded in open-source security because of its flexibility, portability, and robustness. It supports various platforms and operating systems, making it a versatile network security toolkit for security professionals. Its ability to detect cybersecurity vulnerabilities and provide detailed reports makes it a critical tool for network administrators and security analysts. Additionally, the tool's open-source nature allows for continual development and customization, enabling the security community to stay ahead of emerging network security threats.
OpenSCAP Open Source Vulnerability Scanner

OpenSCAP is an open-source vulnerability scanner highly regarded for data and network security. It provides automated compliance checking, vulnerability scanning, and configuration management for enterprise environments.
Here are OpenSCAP’s key benefits:
- Support for multiple operating systems and platforms.
- Automated compliance checking with various security standards, including PCI-DSS and CIS benchmarks.
- Configuration management capabilities for large-scale environments.
- Integration with other network security toolkits and cloud security frameworks.
- Open-source nature allows for continuous development and customization.
OpenSCAP has comprehensive compliance-checking capabilities and can manage configurations across multiple systems. It can also scan for known cybersecurity vulnerabilities and suggest remediation steps. The tool's modular architecture allows for easy customization and integration with other security options, making it a versatile and valuable asset for security professionals.

OpenVAS Open Source Vulnerability Scanner
OpenVAS is a comprehensive open-source vulnerability scanner and management system. It is offered free of charge, licensed under GNU General Public License (GPL), and helpful in supporting different operating systems, including multiple Linux distros.
OpenVAS utilizes an automatically updated community-sourced vulnerability database of over 50,000 known Network Vulnerability Tests. OpenVAS thoroughly examines the entire system and tests authenticated and unauthenticated protocols. The online vulnerability scanning is incredibly detailed, providing an in-depth analysis of how well-guarded the computer and servers are.
 OpenVAS can operate from external servers to help you see exploits in cybersecurity from a hacker's point of view, giving you a chance to utilize security patching before an issue occurs.
OpenVAS can operate from external servers to help you see exploits in cybersecurity from a hacker's point of view, giving you a chance to utilize security patching before an issue occurs.
Some of the critical benefits of OpenVAS include:
- Support for multiple operating systems and platforms.
- Ability to scan for over 50,000 known vulnerabilities.
- Customizable scanning options and reports.
- Integration with other network security toolkits and cloud security frameworks.
- Open-source nature allows for continuous development and improvement.
OpenVAS can provide detailed reports on cybersecurity vulnerabilities and suggest remediation steps. It can also scan for configuration network security issues and check compliance with security standards like CIS benchmarks. The tool's modular architecture allows for easy customization and integration with other security tools, making it a versatile and valuable asset for security professionals.
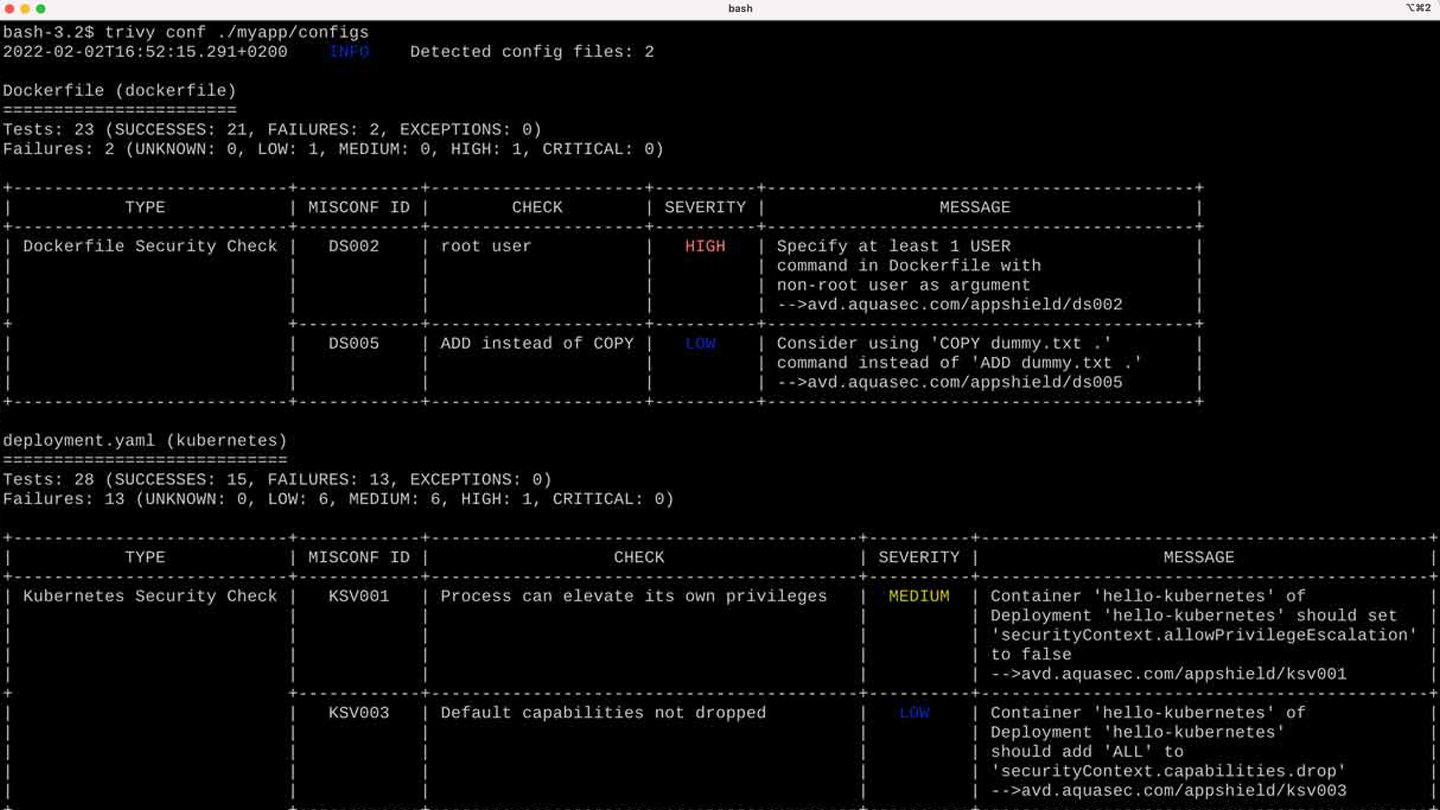
Trivy Open Source Vulnerability Scanner
Trivy is an open-source vulnerability scanner that detects CVEs in open-source software. It provides a quick explanation of network security issues so developers can decide whether to use Trivy in their containers and applications for security patching.
While the usual container security protocols use a static image scan to find cybersecurity vulnerabilities, Trivy seamlessly merges the online vulnerability scanning tool into the Integrated Development Environment (IDE).
With the vast open-source community, many integrations and add-ons support Trivy. Helm chart installs Trivy to a Kubernetes cluster and Prometheus exporter to extract vulnerability metrics.
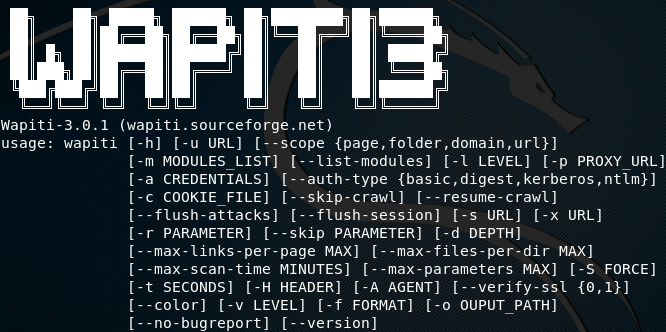
Wapiti Open Source Vulnerability Scanner
 Wapiti is a highly regarded open-source vulnerability scanner that identifies web application security vulnerabilities. Its main benefits include its accuracy, speed, and flexibility, making it a valuable online vulnerability scanning tool for security professionals.
Wapiti is a highly regarded open-source vulnerability scanner that identifies web application security vulnerabilities. Its main benefits include its accuracy, speed, and flexibility, making it a valuable online vulnerability scanning tool for security professionals.
Here are Wapiti’s key benefits:
- Comprehensive coverage of web cybersecurity vulnerabilities, including SQL injection, Cross-Site Scripting, and file inclusion issues.
- Support for both static and dynamic content.
- Customizable scanning options and reports.
- Integration with other network security toolkits and cloud security frameworks.
- User-friendly interface with extensive documentation and tutorials.
Wapiti has an advanced scanning engine that uses a combination of heuristics and signatures to identify cybersecurity vulnerabilities. Its modular architecture allows for easy customization and integration with other security tools, making it a versatile and valuable asset for security professionals. While Wapiti is not explicitly designed to detect wifi and wireless network security issues, it is highly effective in identifying web application security vulnerabilities that could be exploited through wifi or wireless attacks in network security.
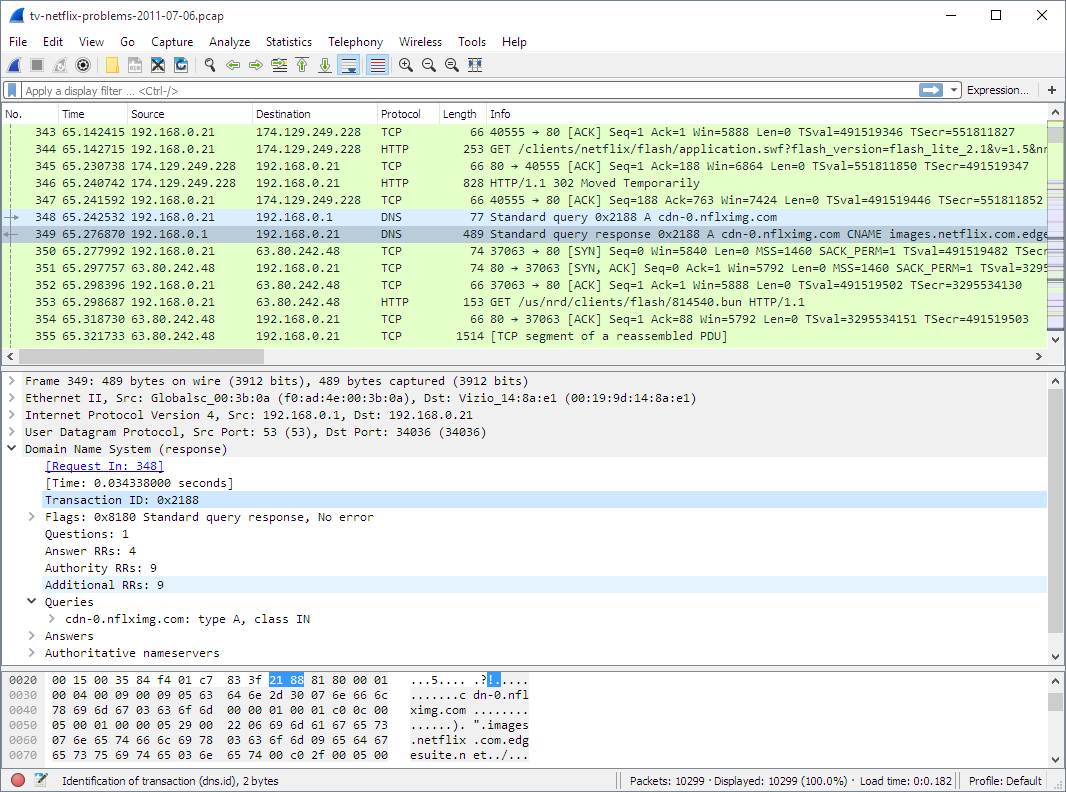
Wireshark Open Source Protocol Analyzer
Wireshark is a free and open-source network vulnerability scanner trusted and used by many governmental and educational institutions. It looks into cybersecurity vulnerabilities at a microscopic level, ensuring a high level of data and network security for your b usiness. To analyze the gathered data, Wireshark captures all network traffic, including Bluetooth, wireless, ethernet, token ring, and frame relay connections.
usiness. To analyze the gathered data, Wireshark captures all network traffic, including Bluetooth, wireless, ethernet, token ring, and frame relay connections.
Wireshark runs smoothly on various platforms, including Solaris. The generated analysis report can be converted into simple and plain text, allowing users with no technical background to understand it better.
Here are Wireshark’s key benefits:
- Ability to capture and analyze network traffic in real-time so it can identify network security threats within your infrastructure
- Support for a wide range of protocols, including wifi and wireless protocols.
- Customizable filtering and analysis options.
- Graphical visualization of network traffic patterns and anomalies.
- Extensive documentation and community support.
- Optimize network performance by identifying bottlenecks or other network security issues impacting network speed and reliability.
Wireshark provides a detailed network traffic analysis, making it a valuable tool for identifying potential web application security vulnerabilities and investigating security incidents. While it is not explicitly designed to detect wifi and wireless vulnerabilities, its support for wifi and wireless protocols makes it highly effective in analyzing and identifying potential cybersecurity vulnerabilities.
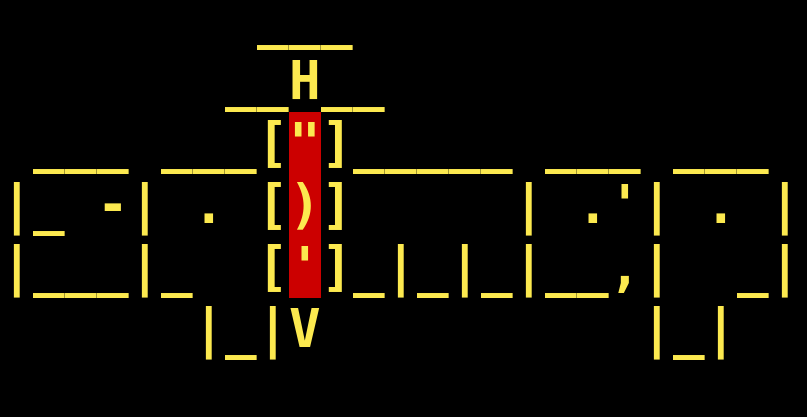
sqlmap Open Source Vulnerability Scanner
Sqlmap is a penetration testing tool with features that automatically detect and evaluate cybersecurity vulnerabilities. It goes beyond finding network security issues by attempting to exploit them to create a detailed report on the results.
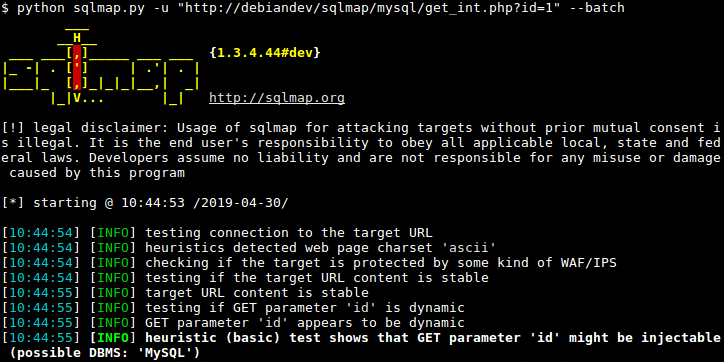
 Sqlmap was developed in Python, supporting any operating system with a Python interpreter installed. Using six different methods, it will automatically recognize password hashes and exploit SQL injection vulnerabilities. An SQL injection (SQLi) attack is a web-based attack that targets databases by inserting malicious code into SQL statements through a web application's input forms or other user input fields.
Sqlmap was developed in Python, supporting any operating system with a Python interpreter installed. Using six different methods, it will automatically recognize password hashes and exploit SQL injection vulnerabilities. An SQL injection (SQLi) attack is a web-based attack that targets databases by inserting malicious code into SQL statements through a web application's input forms or other user input fields.
An SQL injection attack aims to manipulate the database in a way not intended by the web application's developers, allowing the attacker to extract sensitive information, modify or delete data, or even take control of the entire system.
SQL injection attacks can occur in a variety of environments:
- Web applications that rely on user input, such as search forms or login pages.
- Content Management Systems (CMS) and e-commerce platforms that allow users to create and edit content or product listings.
- Legacy systems that use outdated database technologies or programming languages.
- Mobile applications that interact with a backend database through APIs.
SQL injection attacks in network security can be prevented through various security measures, such as input validation and parameterized queries. Developers and system administrators must know the potential risks of SQL injection attacks and take proactive steps to secure their systems. The tool has a comprehensive database that supports Oracle, PostgreSQL, MySQL, SQL Server, and Access.
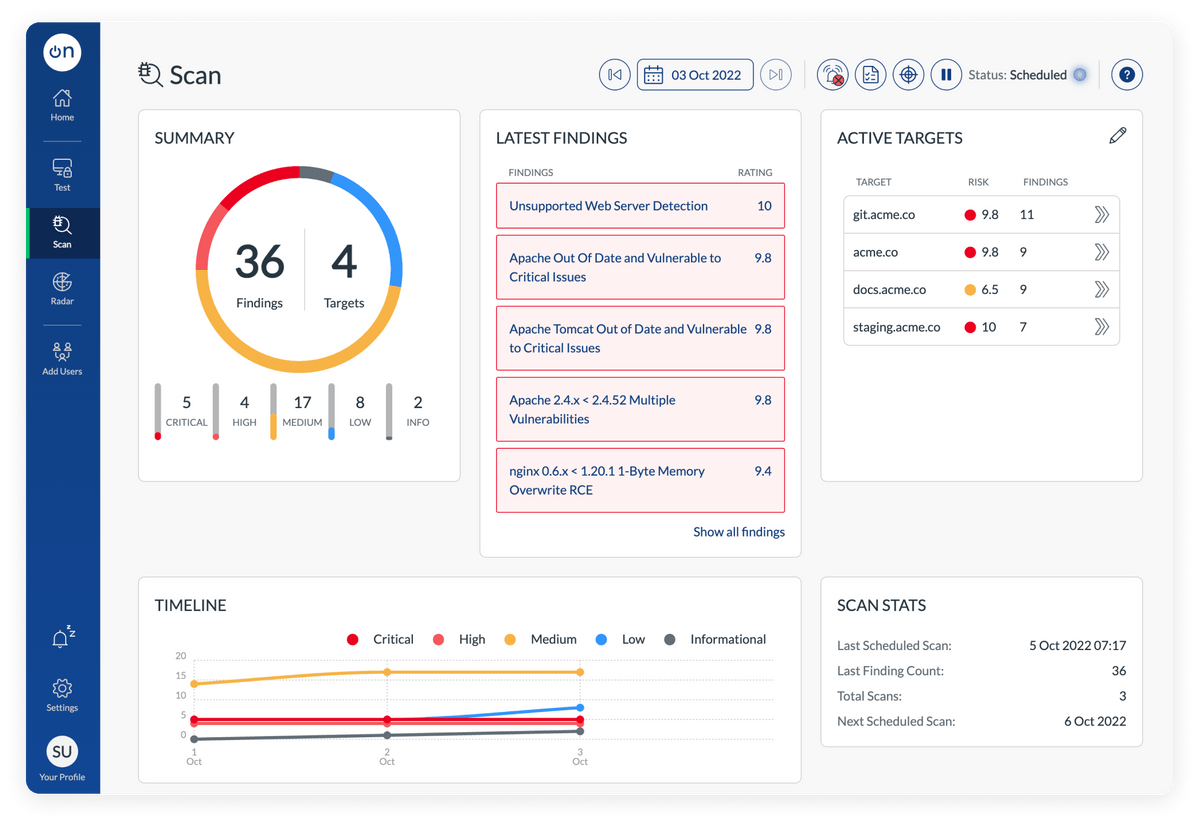
Honorable Mention: OnSecurity Vulnerability Scanner
Online vulnerability scanning with OnSecurity carries out over 40,000 checks for missing patches, security misconfigurations, default passwords, and dangerous passwords. It regularly monitors your system, scans your internet-facing assets, and identifies cybersecurity vulnerabilities before an attacker can exploit them. Vulnerability scanning tools help identify areas you can improve and provide an inventory of assets. Plus, the OnSecurity Portal dashboard rates each vulnerability with a CVSS score, helping you to prioritize and understand your risk. OnSecurity will notify you through an in-portal, SMS, or Slack as soon as a finding is discovered so you can take immediate action.
Final Thoughts on Using Open-Source Vulnerability Scanning Tools to Secure Your Linux Systems

Online vulnerability scanning is critical in protecting an organization from threat actors. It helps identify network security issues and cybersecurity vulnerabilities in the organization's systems and applications. With vulnerability scanning tools, an organization may be aware of potential network security threats that attackers could utilize, leading to data and cloud security breaches, system compromise, and other exploits in cybersecurity.
Open-source vulnerability testing tools like Wireshark, OpenVAS, and Nmap are critical instruments for an open-source security practitioner to check for these cybersecurity vulnerabilities because they provide a comprehensive view of the organization's network and systems. These network security toolkits allow security practitioners to identify and assess web application security vulnerabilities, including weaknesses in system configurations, out-of-date software versions, and network misconfigurations. They also enable practitioners to prioritize and remediate data and network security issues quickly, reducing the organization's attack surface.
Using open-source vulnerability scanning tools is particularly advantageous because they are free and often have a robust user community contributing to their development and maintenance. This means they are continuously updated and refined, making them more effective at detecting and addressing emerging network security threats. Additionally, open-source tools are often more transparent and customizable, allowing security practitioners to adapt them to their specific needs and workflows to improve security posture overall.