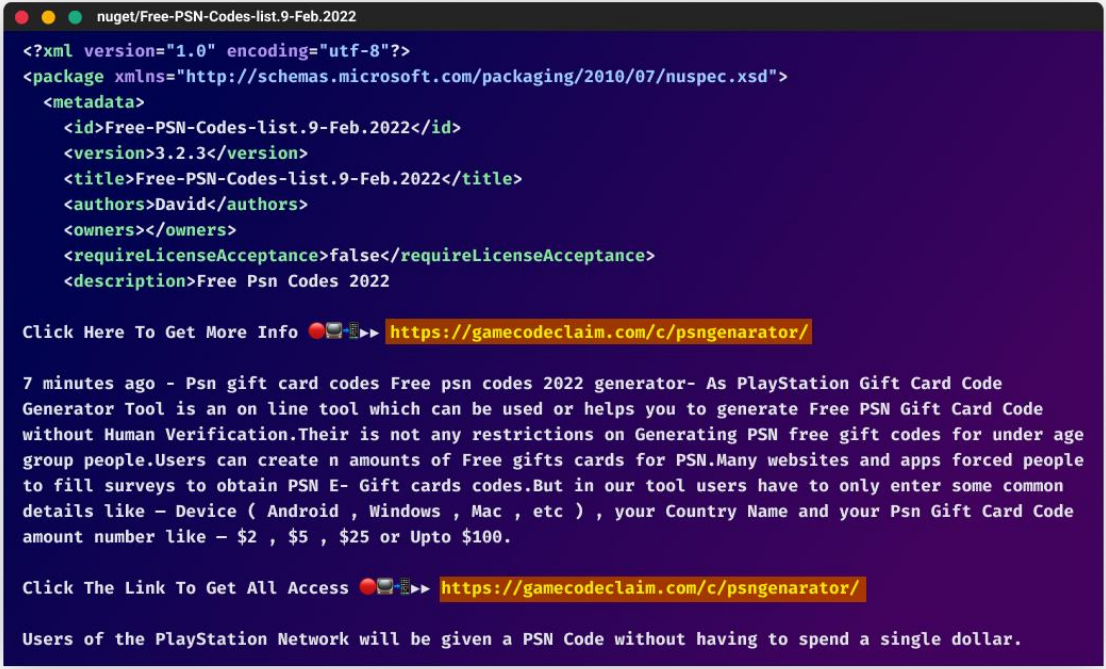
Large-Scale Phishing Campaign Floods Open-Source Repositories with 144,000 Packages

Researchers have identified that unknown threat actors uploaded about 144,294 phishing-related packages using open-source package repositories, including NPM, PyPi, and NuGet. Automation allowed for these large-scale attacks in network security that promoted fake apps, prize-winning surveys, gift cards, giveaways, and more. Hackers utilized naming schemes with similar features in the descriptions to host over 65,000 phishing pages across 90 domains.
A Massive Example of the Growing Phishing Problem
Phishing exploits in cybersecurity impact the open-source software ecosystem by accounting for over 90% of today’s cyberattacks in network security, posing a threat to all users and organizations. The quantities for malicious package uploads are as follows: NuGet had 136,258, PyPI had 7,894, and NPM had 212 infections. The package descriptions contained phishing site URLs and urged users to click links for details about alleged gift card codes, applications, and hacking tools.
Security professionals discerned that attackers were focusing on increasing the SEO of their phishing sites. Almost all of these sites request visitors to enter their email, username, and account passwords, causing victims to share sensitive data that hackers monetize for personal and financial gain. The system then initiates a series of redirects to survey sites, landing on legitimate e-commerce websites using affiliate links that generate revenue for the malicious actors. If victims made purchases on these sites while the referral codes were active, the threat actors would receive referral awards, making the safe website a distraction for this secondary exploitation scheme of stealing a victim’s login credentials.
The Bottom Line
Online repositories removed these phishing campaign packages from their sites, but NuGet unlisted them from search results, meaning they are still available but difficult to access. However, these automation methods for phishing raise concern for security professionals, who worry that cybercriminals could reintroduce these network security threats easily and work quickly to harm data and network security once more. Linux security expert Dave Wreski advises, “To protect their digital security, users should always engage in cybersecurity best practices and remain vigilant when browsing package repositories.”
Check out this IoC text file on GitHub for the complete list of URLs used in this campaign. Be sure to visit LinuxSecurity.com frequently and subscribe to our weekly newsletters to stay up-to-date on the latest security news and information impacting the open-source community!