A Complete Guide to Security Automation & Reporting Using Open-Source Tools

Open-source security automation is a critical aspect of modern cybersecurity. Various data and network security tasks, including vulnerability scanning, incident response, and compliance monitoring, employ open-source tools and technologies to improve efficiency and effectiveness throughout security operations.
Cyber fraud typically targets medium- to small-sized businesses because such companies often lack the resources and expertise to protect themselves adequately from exploits in cybersecurity. However, open-source security automation network security toolkits can help reduce web application security vulnerabilities. These tools can detect and report network security issues and automatically patch such risks, minimizing the chances of a successful attack. This article will discuss the value of security automation and introduce several open-source security automation tools to protect against cybersecurity vulnerabilities.
Why Is Open-Source Security Automation Critical for Robust Cybersecurity?
Open-source security automation helps organizations find network security threats faster, a crucial benefit in today's fast-paced digital environment. Developers uncover discoveries frequently, so companies must identify and mitigate network security issues as quickly as possible. These network security toolkits can regularly scan a business' IT infrastructure for cybersecurity vulnerabilities so they can utilize security patching immediately before any problems arise. Since these open-source security automation tools can deal with security incidents more efficiently, data and network security incidents have less impact on organizations, allowing companies to continue functioning as usual.
Here are a few benefits of using open-source security automation tools in a security plan:
- Scalability: Scan large and complex environments (cloud and/or hybrid) with interconnected systems to comprehensively view network security threats.
- Cost-effectiveness: Typically available at no cost, these tools are affordable for companies of any size.
- Customizability: Customize and configure the tools based on the organization's specific needs for more targeted and adequate security measures.
- Community support: Users and developers maintain servers with their wealth of knowledge and resources for troubleshooting and problem-solving.
- Compliance: Help companies comply with industry regulations and standards like PCI-DSS, HIPAA, and SOC2
- Continuous monitoring: Continuous monitoring and alerting allow quick responses to potential network security threats and other cybersecurity vulnerabilities.
- Integration: Blend tools with other network security toolkits (like SIEMs) to comprehensively view network security issues.
- Threat intelligence: Leverage threat intelligence feeds and databases to identify the latest problems headed your way.
Types of Security Automation Tools
Here are a few security automation options and the tools and technologies they integrate:
- Network security automation executes tasks like firewall management, intrusion detection, and vulnerability scanning.
- Endpoint security automation employs antivirus software, patch management, and endpoint configuration management.
- SIEM automation involves collecting, analyzing, and reporting security-related data.
Open-Source Security Automation Projects and Organizations
Multiple open-source projects exist to work with the community on developing and promoting open-source security automation tools.
OWASP is a non-profit organization that aims to improve security posture through software updates that offer a range of resources and tools for developers and security professionals. The organization has various projects focusing on web application security vulnerabilities. The OWASP Top 10 Project identifies the most significant network security issues to remember.
The Open-Source Security Testing Methodology Manual (OSSTMM) provides testing and assessment frameworks to analyze systems and applications so security professionals can utilize their open-source methodology to care for security patching before network security threats become an issue.
The Community for Open-Source Security Automation Software (COSSAS) offers a continuously expanding base of novel software components for cybersecurity automation that SOC, CERT, and CTI professionals can deploy and trial in their operational environments.
These organizations have many open-source security automation resources, such as guidelines, best practices, and identification and mitigation tools. This information can strengthen companies’ data and network security throughout their systems and applications.
Top Open Source Security Automation Tools
Here are a few of the most popular and widely used tools to consider out of the various open-source security automation tools offered online:
OWASP ZAP Web Application Security Scanner
OWASP Zed Attack Proxy (ZAP) is a security scanner that can identify web application security vulnerabilities by:
- Actively interacting with web applications to detect SQL injection, Cross-Site Scripting (XSS), and broken authentication or authorization.
- Implementing features like a proxy server, automated scanner, or API with other tools to find network security threats faster.
- Providing a user-friendly, navigable interface with cybersecurity vulnerabilities access.
- Regularly updating with new features and security checks for finding and staying up-to-date on the latest network security issues.
- Running on various platforms like Windows, Linux, and Mac OS and integrating with CI/CD pipelines for continuous scanning.
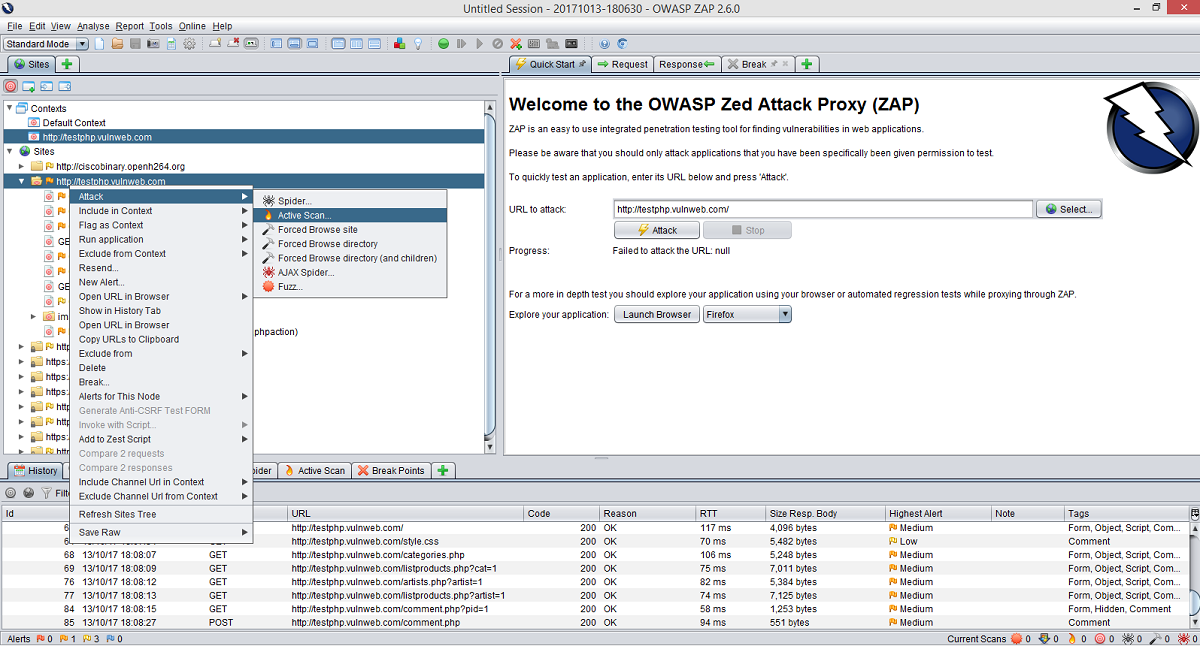
OWASP ZAP can also use cloud security frameworks like Ruby on Rails and ASP.NET to find other possible exploits in cybersecurity, making it an incredibly beneficial, universal tool.
OpenVAS Open Source Security Automation Scanner
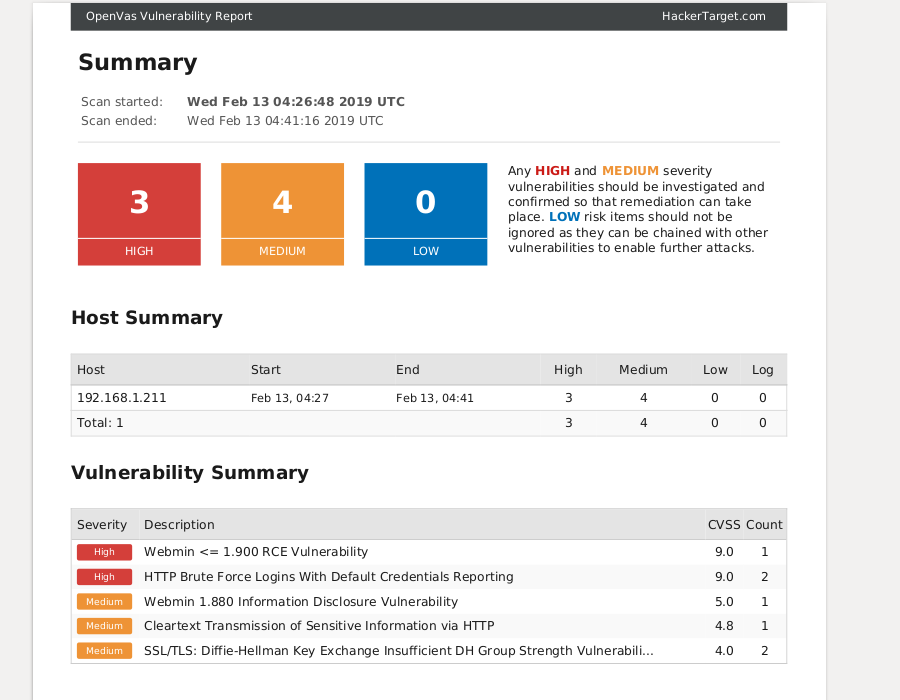
OpenVAS (Open Vulnerability Assessment System) is a full-featured cloud security scanner that can scan networks and hosts for known cybersecurity vulnerabilities. It uses an extensive collection of Network Vulnerability Tests (NVTs) to scan for network security threats and software misconfigurations. OpenVAS can scan servers, workstations, and network devices, identify missing security patches, and notify companies about configuration issues that may leave a system vulnerable to attacks in network security.
security patches, and notify companies about configuration issues that may leave a system vulnerable to attacks in network security.
The software uses a client-server architecture where a central management server and a scanner engine work together when performing vulnerability scans to analyze. Such information can be reported through built-in capabilities or exports, which can help users improve security posture. OpenVAS has a flexible, customizable framework allowing users to create their scan configurations and adapt them to their specific needs and environments.
Here are the benefits OpenVAS offers to users:
- Scheduled Scans: Configure OpenVAS to perform scans at regular intervals (daily or weekly) to promptly identify and address cybersecurity vulnerabilities.
- Targeted Scans: Specify targets in scanning (certain IP addresses or URLs) to focus on one type of web application or system.
- Continuous Scans: Perform scans constantly to find network security issues as they enter a web application.
- Baseline Scans: Establish a baseline of web application security vulnerabilities to keep track of when identifying network security threats over time.
- Compliance Scans: Check for compliance with industry standards and regulations, including PCI-DSS and HIPAA.
- Custom Scans: Create custom configurations to scan a web server or database for specific cybersecurity vulnerabilities.
- Integration with other tools: Integrate with network security toolkits to get more comprehensive views on data and network security risks.
- Automated reporting: Generate reports that can document and track progress in addressing vulnerabilities, which can help demonstrate compliance with regulations and understand the effectiveness of security measures.
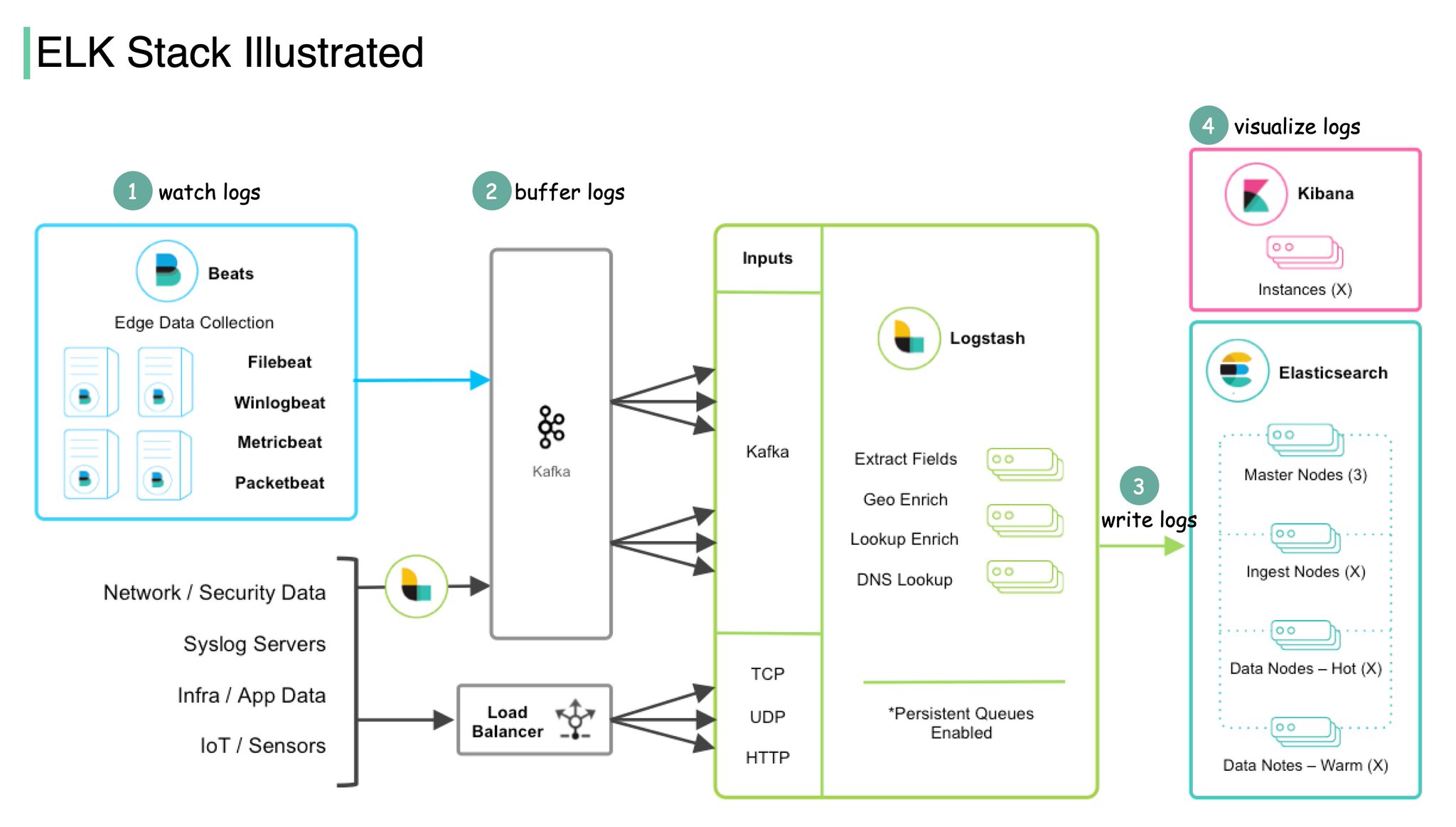
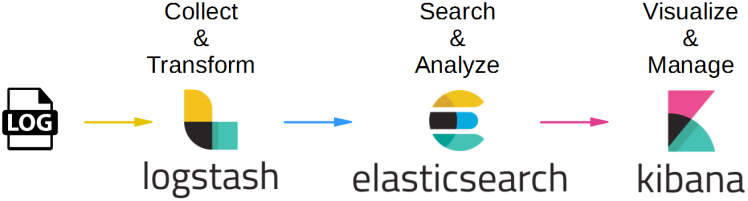
Elasticsearch, Logstash and Kibana (ELK) Open Source Log Management
The ELK (Elasticsearch, Logstash, Kibana) stack is a popular open-source log management and analysis tool that can collect such information through servers, firewalls, and intrusion detection systems. Organizations can quickly identify and respond to security incidents once the ELK stack analyzes a server for web application security vulnerabilities. This can prevent exploits in cybersecurity that could cause problems for the company.
Here are the benefits of using ELK stack:
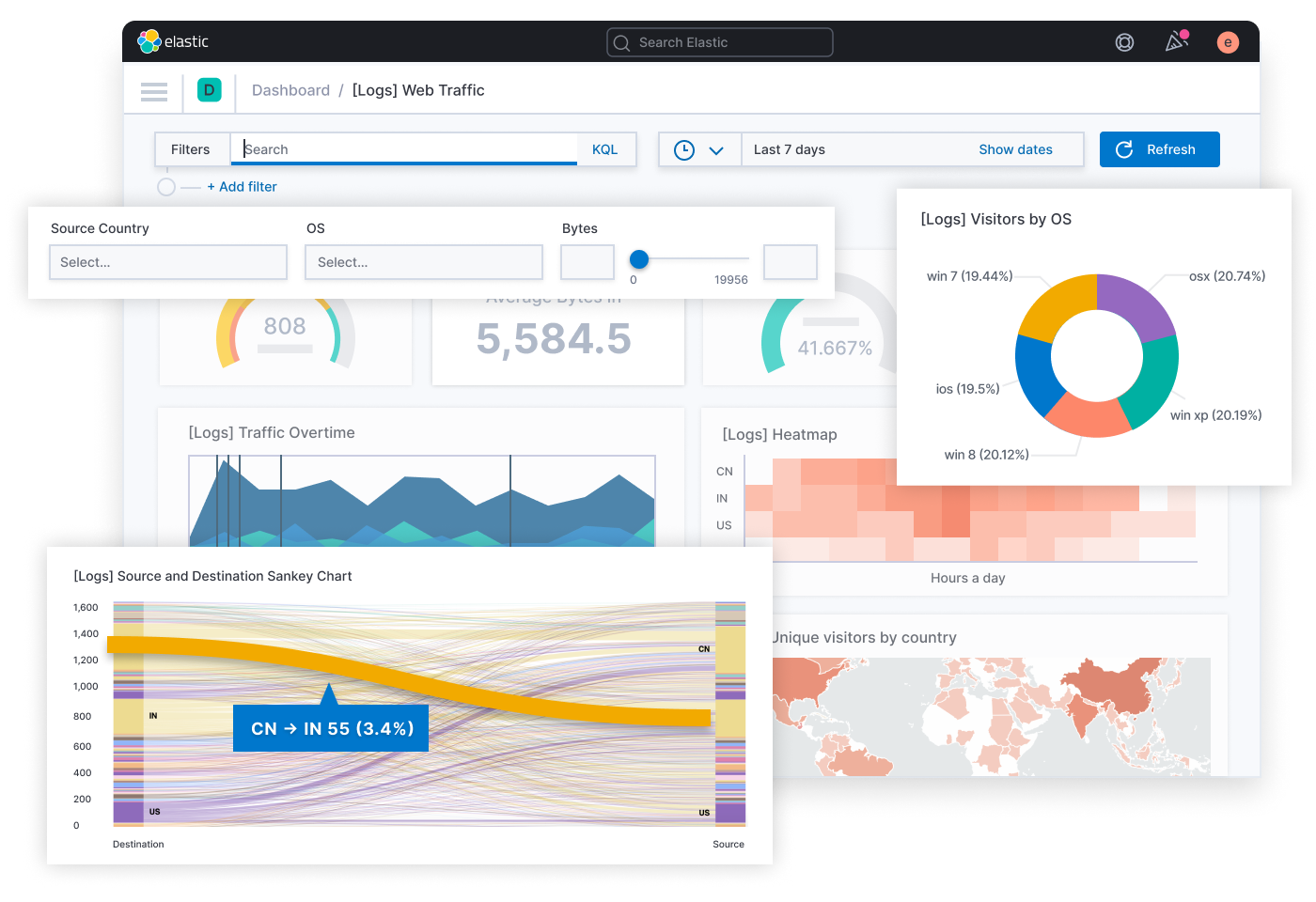
- Various built-in tools: Elasticsearch indexes and stores log data and analysis. Logstash collects and processes log data. Kibana visualizes and analyzes data.
- Log data analysis: Find and identify cybersecurity vulnerabilities after using tools to monitor suspicious activity like failed login attempts or unusual network traffic.
- Vulnerability detection: Look at log data for alarming patterns or anomalies.
- Automation: Use Machine Learning (ML) algorithms and anomaly detection techniques to flag potential network security issues.
- Open-source community: Contribute to the stack and its capabilities to improve security posture, adapt your services to network security threats, and stay up-to-date on web application security vulnerabilities evolving in the online landscape.
Ansible Open Source Security Automation
The Ansible automation tool patches server vulnerabilities handles configuration management and application deployment, and automates tasks. Companies can reduce their risk of attacks in network security by having this service identify network security issues quickly so that security patching can mitigate the risks efficiently.
Here are the main benefits of using Ansible:
- Security automation: Set up an automatic process for configuring and maintaining your organization’s systems.
- Security policies: Use code to ensure data and network security configurations are performed safely.
- Identify web application security vulnerabilities: Have online and cloud security audits check your servers for network security threats regularly.
- System monitoring: Identify changes that indicate a vulnerability.
- Use predefined playbooks: Automatically respond to critical network security issues and remediate vulnerabilities.
- Integration: Use with other security tools on Windows and Linux servers, network devices, and in cloud environments.
Other Open Source Security Automation Tools
Many open-source tools can be used for endpoint security, SIEM (Security Information and Event Management), and network security automation. Here are a few more tools to consider when choosing one for your business:
- Suricata: A high-performance network IDS, IPS, and network security monitoring engine.
- Snort: A rule-based network intrusion detection and prevention system.
- OSSEC: A Host-Based Intrusion Detection System (HIDS) that monitors and analyzes log files from various systems and applications.
- SELKS: A security distribution based on Debian that includes Suricata, Elasticsearch, Logstash, and Kibana (ELK Stack)
- Nagios: A network and system monitoring tool that monitors and alerts on various network and system metrics.
- Wireshark: A powerful packet analyzer that analyzes and troubleshoots network traffic.
- Nmap: A popular network scanner that maps networks and identifies hosts, services, and vulnerabilities.
- Nessus: A vulnerability scanner that identifies web application security vulnerabilities in systems.
- Metasploit: A penetration testing framework that finds exploits in cybersecurity systems and applications.
- Wapiti: A web application security scanner that notifies users of vulnerabilities by performing black box testing.
Final Thoughts on Security Automation & Reporting Using Open Source Tools
Open-source security automation is a powerful tool that can protect businesses from various cybersecurity vulnerabilities. By using tools such as OWASP ZAP, OpenVAS, Ansible, and the ELK stack, organizations can detect and report network security issues in web applications and servers efficiently. These tools offer security patching to address network security threats before an attack. Medium- to small-sized businesses are particularly vulnerable to cyber fraud, and using these open-source tools can help protect these businesses from potential attacks in network security.





















