Email Phishing Using Kali Linux

So long as you navigate the Internet, you will encounter a phishing attack attempt sooner or later. Cybersecurity professionals seek solutions to these threats so that attacks in network security are not as common and harmful to online users.
Phishing can be highly damaging and have widespread consequences for victim organizations, including financial losses, data theft, and severe reputational harm. Therefore, companies have incorporated network security training courses for employees to respond to an attack appropriately. Cybersecurity teams send spoofed emails, create fake login pages, and otherwise behave as genuine scammers so they can test how workers mitigate an attack.
Kali Linux is an open-source, Debian-based Linux security training platform for digital forensics and penetration tests. Using open-source network security toolkits with Kali Linux allows people to run phishing simulations so companies can identify cybersecurity vulnerabilities and take care of them immediately, reducing the chance of a phishing attack. This article will discuss how you can conduct your own email phishing training using open-source tools on Kali Linux to help improve your organization's security posture, protect against cyberattacks, and mitigate data and cloud security breaches.
What Is Email Phishing?
Email phishing occurs when cybercriminals create fake emails to get recipients to provide personal details and sensitive information that malicious parties can later use in exploits in cybersecurity. Phishing targets generally receive urgently toned messages claiming to contain information regarding a missed delivery, a late payment, or an unfulfilled order. Some phishing attacks take a positive approach by asking victims to provide information in exchange for supposed prizes or funds.
When victims click on the links in a message, hackers redirect the user to phishing pages where threat actors can harvest sensitive information without the user’s knowledge. Phishing attacks could ask recipients to download seemingly harmless files that contain malware to infect entire networks. Over ninety percent of modern cyberattacks begin with a phishing email due to their effectiveness in execution.
What Best Practices Help Combat Phishing Attacks?
Whether you’re an individual user or involved with organizational cybersecurity, it is vital to engage in the best email security practices that will keep you safe and set an example for your employees on how to avoid an attack:
- Check the legitimacy of an email before immediately trusting the content.
- Understand the components of a phishing email.
- Only open links and attachments that are not suspicious.
- Apply electronic signatures to emailed documents to protect your messages.
- Schedule regular employee Linux security training sessions and utilize privacy sandboxing tactics to discuss how to handle an attack with phishing simulations.
- Install a spam filter to screen for malicious content in your system.
- Look out for and report well-known and emerging phishing network security threats.
- View phishing prevention as everyone's responsibility.
- Implement a comprehensive, adaptive, cloud-based email security solution.
While these security practices cannot wholly stop attacks in network security, they can significantly reduce the likeliness of a successful attack. Teaching your employees how to take phishing prevention seriously can assist your company in recognizing and stopping more cloud security breaches and issues.
Why Is Security Awareness Training Critically Important?
Security Awareness Training (SAT) is an organization-wide effort that helps people identify and protect themselves against network security threats at work and while using the Internet at home. SAT is an integral part of organizations’ cybersecurity defenses.
A 2022 study that exposed participants to five categories of emails found that people generally had trouble recognizing modern phishing attacks. Although fifty percent of the people identified red flags like spelling and grammar mistakes, more ambiguous and less obvious attacks were challenging to detect.
Organizations must implement SAT because human error is an element in most cyberattacks. The people who organize phishing attacks know how to tap into what people want and what they're most likely to believe. In addition, many people work in high-pressure environments with numerous expectations placed on them. Those realities may mean they need to take more time to study emails to determine validity. However, individuals should get continual education about what constitutes a phishing attack. In that case, they'll be more alert to suspicious characteristics and know not to engage with emails with these data and network security issues.
It's also essential that any SAT efforts center on online threats. Some people spend dozens of hours online weekly, so it's highly likely they'll eventually encounter Internet dangers. Security awareness training will equip each employee to spot and avoid risks. As a result, organizations have better protection from cyberattacks that could halt operations, make them lose money and customers, or mean the business must recover from reputational damage.
How Should I Conduct Email Phishing Training?
Internal testing and Linux security training will help people become more aware of and avoid common email phishing strategies. Fortunately, Kali Linux is a great network security toolkit that offers excellent open-source options that help facilitate phishing training.
Running phishing training at your business allows you to create authentic examples of phishing attacks and see how employees respond to them. You can then find gaps in workers’ awareness and focus on those in upcoming training sessions.
What Training Tools Does Kali Linux Offer?
Kali Linux is an open-source distribution toolkit for people who run penetration tests and perform cloud security audits. The service has over six hundred penetration tests that are free to use and easily customizable to an organization's needs. Here are a few of the best phishing tools for Kali Linux users:
PhishMailer
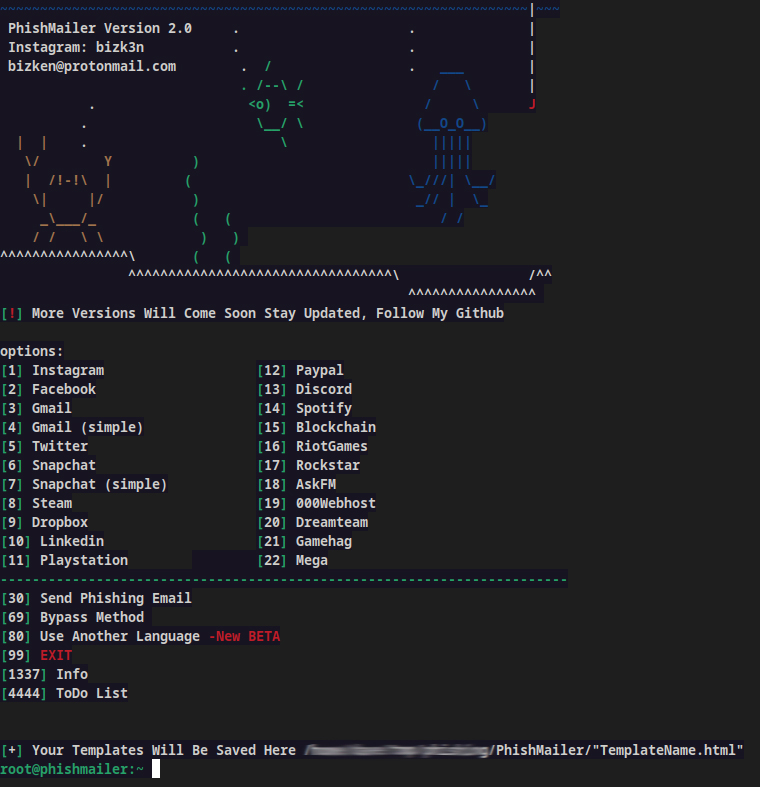
PhishMailer allows you to create email templates from more than 20 well-known companies. Python 3 developers tested this tool, and you need Python 3 software. While Phishmailer is a user-friendly interface, there have been no updates for years.
Install it by cloning the repository with the git clone command:
git clone https://github.com/BiZken/PhishMailer
The following command will install it and let you access the tool’s directory:
cd Desktop git clone https://github.com/BiZken/PhishMailer cd PhishMailer/
Now that you've downloaded the tool, run it with the following command:
python3 PhishMailer.py
You’ll then have the opportunity to enter several pieces of information about your phishing target so you can simulate attacks in network security effectively.
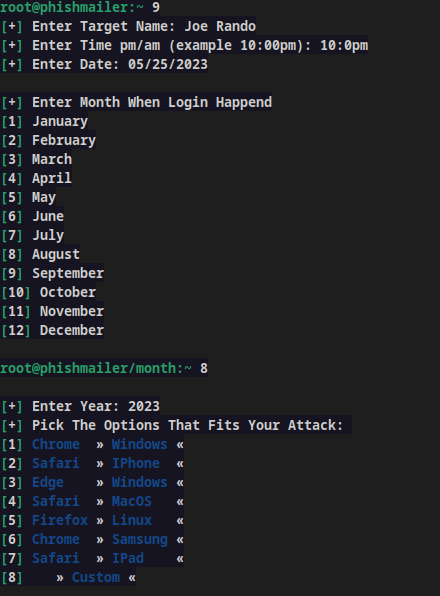
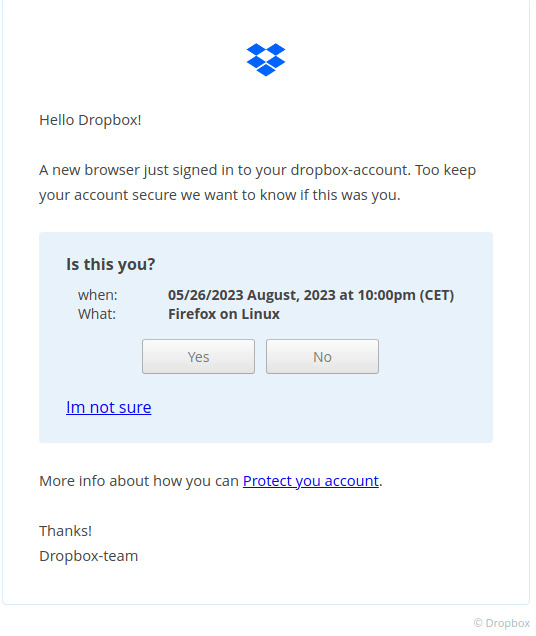
Next, the tool will generate a link you can open in a browser. Once a phishing target enters their email and password on the fake page, you’ll get relevant details, as seen below.
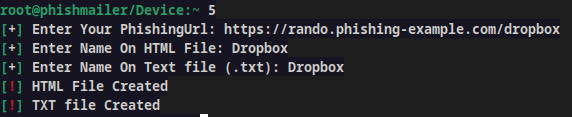
Within two minutes of installing, I created this Dropbox sample phishing message. Each link in this screenshot (even the "I'm not sure" link) directs to my sample phishing site.
BlackPhish
BlackPhish is a robust but lightweight phishing email simulator tool. It is still in the beta testing phase, so there could be network security issues when using it, but it has a user-friendly interface and six email templates. Developers tested it on Kali Linux 2019.4, but compatibility checks on other platforms are ongoing.
Install BlackPhish by moving to the desktop and using the following command:
cd Desktop git clone https://github.com/iinc0gnit0/BlackPhish
While inside the tool’s directory, continue the installation with the following command:
cd Blackphish sudo bash install.sh
Finally, run BlackPhish with the command:
sudo python3 blackphish.py
After doing that, you’ll reach the main screen. Choose the type of phishing simulation you want to make by pressing its corresponding number and the Enter key.
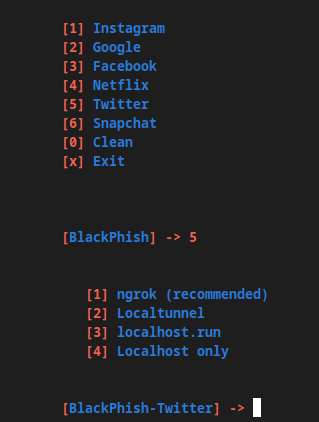
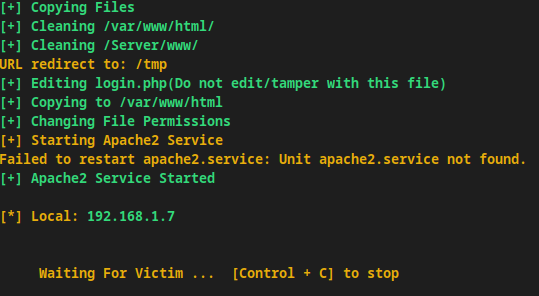
Progressing through the steps will give you further options to customize the content, and you’ll get a preview of how the simulated message will look to users. Eventually, you’ll receive relevant information if someone falls for the phishing trick.
Lockphish
Lockphish creates phishing content that gets placed on a smartphone's lock screen, allowing hackers to gain a phone user's login credentials. Android and iOS smartphones, as well as Windows PC operating systems, can be put to the test with Lockphish. The tool has an IP tracker and can automatically detect the kind of device a person has unless it is a Mac computer, which the server does not pick up.
Start the installation by cloning Lockphish from its GitHub repository with the following command:
git clone https://github.com/jaykali/lockphish.
Then, use this command to reach the Lockphish directory:
cd lockphish
Grant Lockphish root access before running it by using the command:
sudo chmod +x lockphish.sh
Finally, run the tool by inputting:
./lockphish.sh
Doing this will launch the tool’s main screen, as seen below:
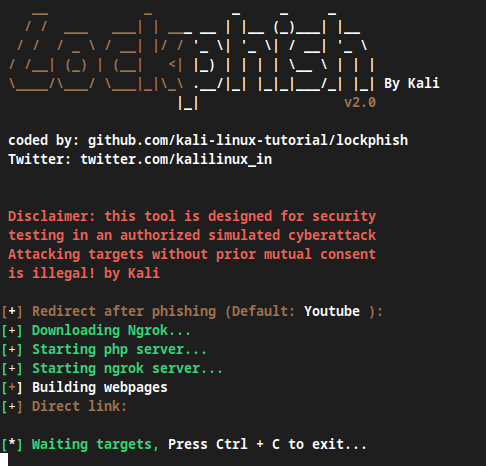
You then need to choose a website that Lockphish will use for their redirect. YouTube is the default selection. Press the Enter key after selecting the desired website, and this will cause ngrok to download within Kali Linux and configure the phishing servers on the local host.
The Lockphish screen will provide you with several options to change the parameters, as shown below:
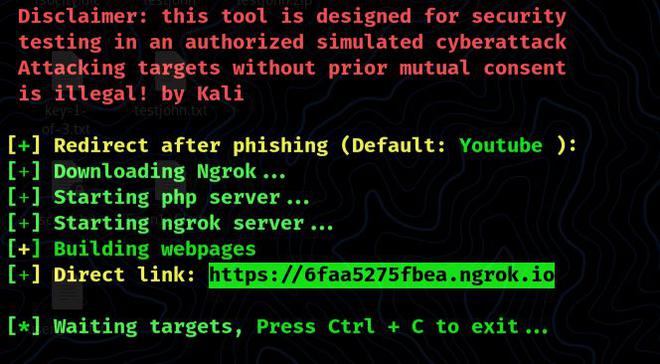
Next, the simulated phishing attack mimics the users’ lock screens. Once a person enters credentials, such information gets captured and reaches the Lockphish user through a ngrok tunnel.
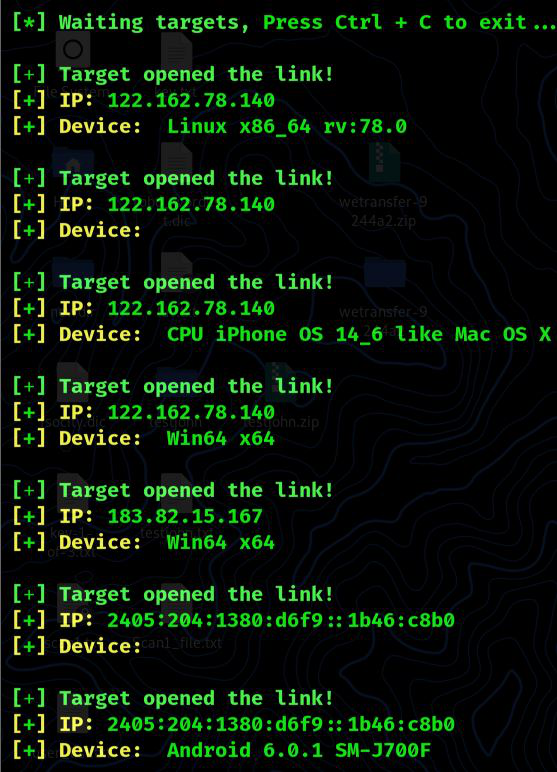
Once a target clicks the phishing link, you’ll get information about them, as shown below.
Socialphish
Socialphish is an open-source tool with over thirty templates for famous websites that users can modify to create believable attacks with which to trick users. This tool is easy to use and only takes up additional space. Written in Python, you can generate phishing websites based on Spotify, Facebook, Instagram, WordPress, Microsoft, and more.
To install Socialphish, move a Kali Linux terminal to your desktop and create a directory titled “Socialphish.”
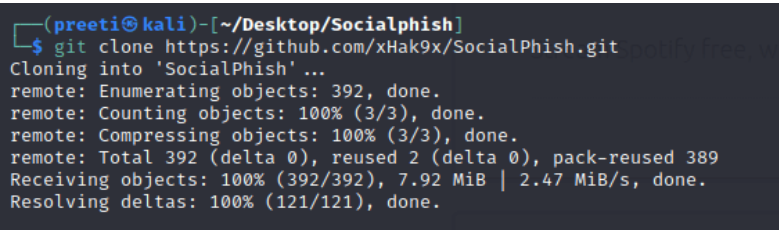
Then enter the Socialphish directory and clone the tool from GitHub phishing with these commands:
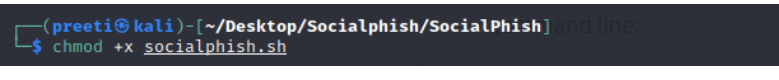
To access the tool’s contents and give permissions, input “ls” and “chmod +x socialphish.sh”
Run the tool by typing in “./socialphish.sh”
Once everything is set up, you can choose a phishing page from the options listed.
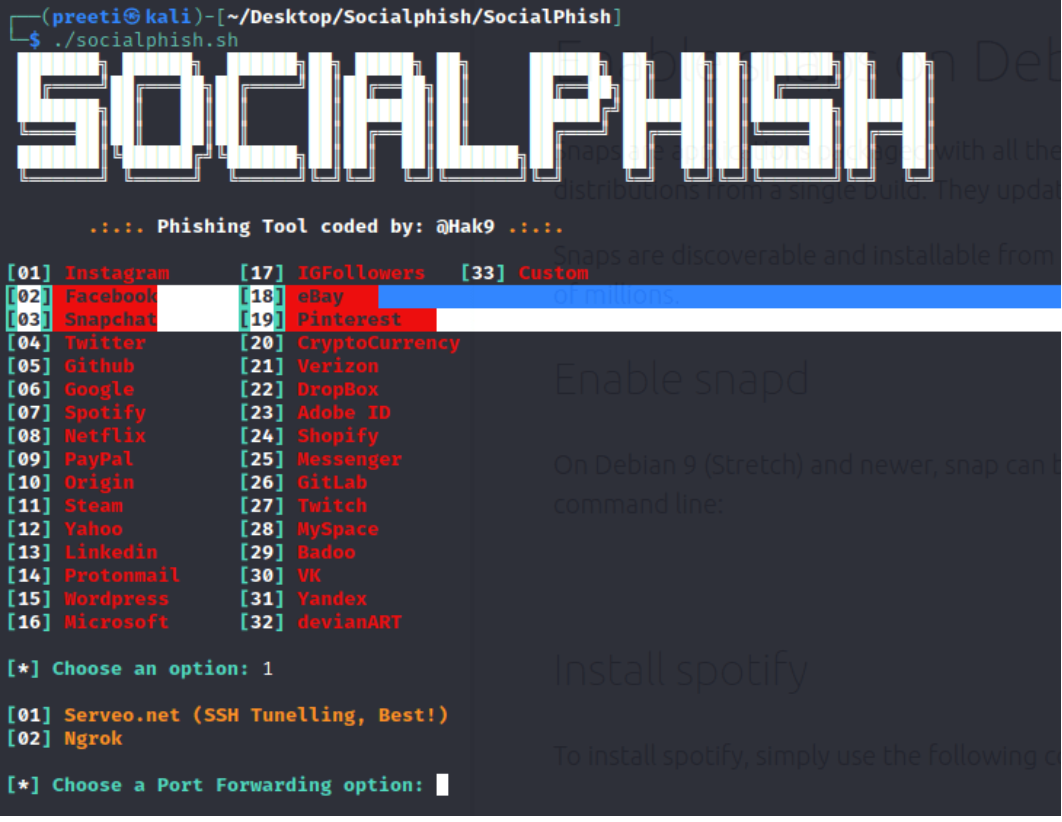
ShellPhish
ShellPhish focuses on impersonating Facebook, Twitter, Instagram, and eighteen other websites with templates that can help companies obtain ID and password credentials.
Install ShellPhish, move it to the Desktop on the Kali Linux terminal, and create a directory.

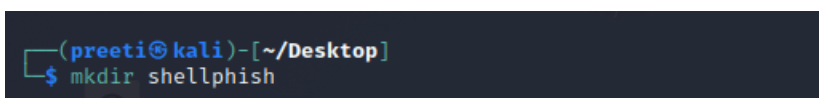
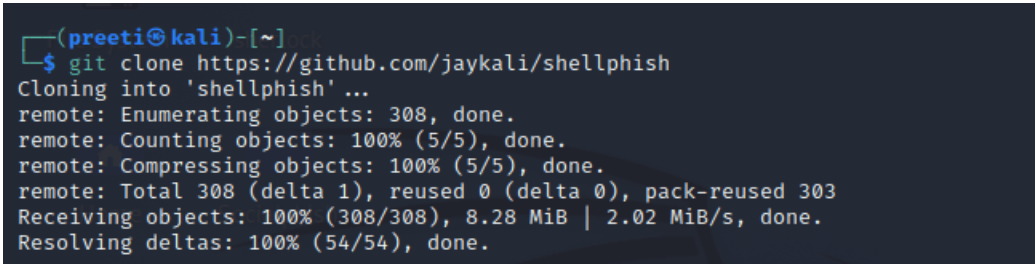
Clone the service and type the commands needed to execute ShellPhish.
Once you have done this, you will see the options from which to choose when deciding on a sandboxing attack.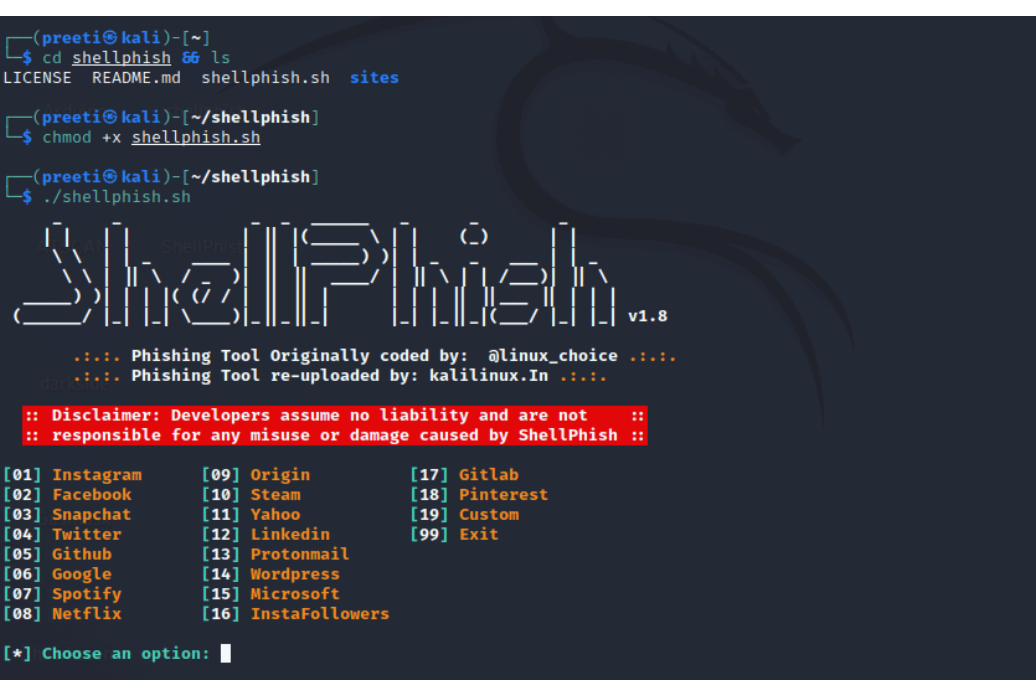
Zphisher
Zphisher grew in popularity following the influx of attacks on Target. With thirty templates and easy navigation tools, Zphisher is a favorite for testing data retrieval attempts. The service also has frequent updates that help you work with the most recent options available.
Like with other tools, install the server, move it to your desktop, and clone the directory so you can run the command on your computer.
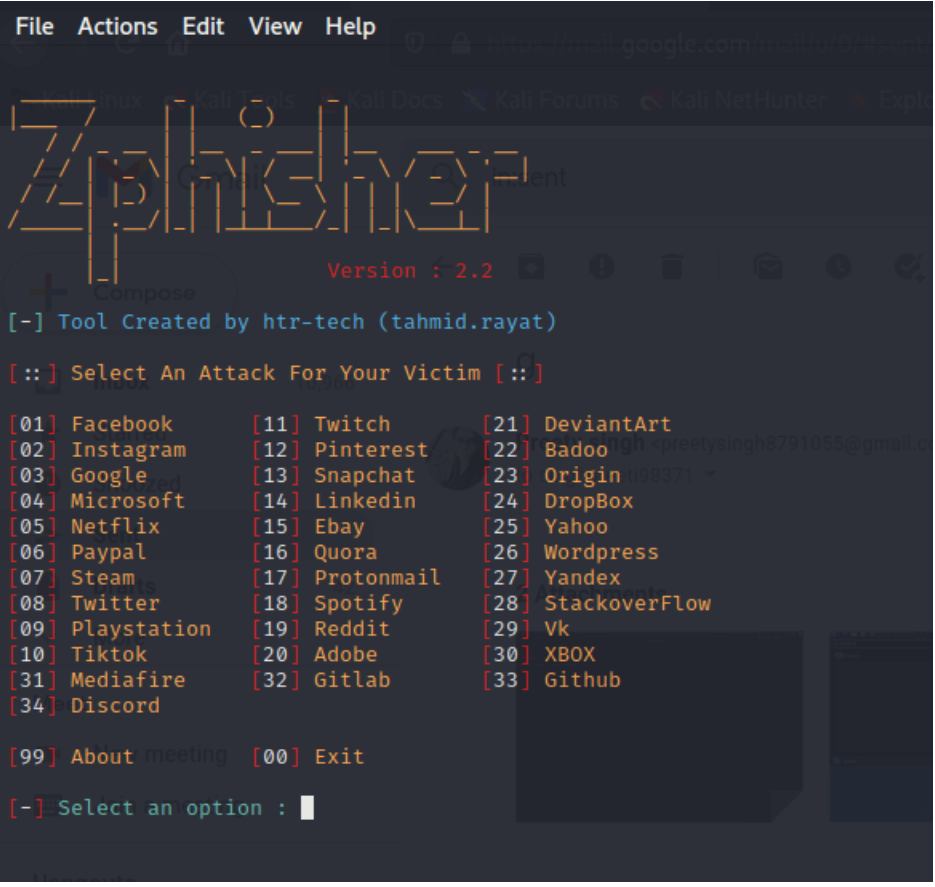
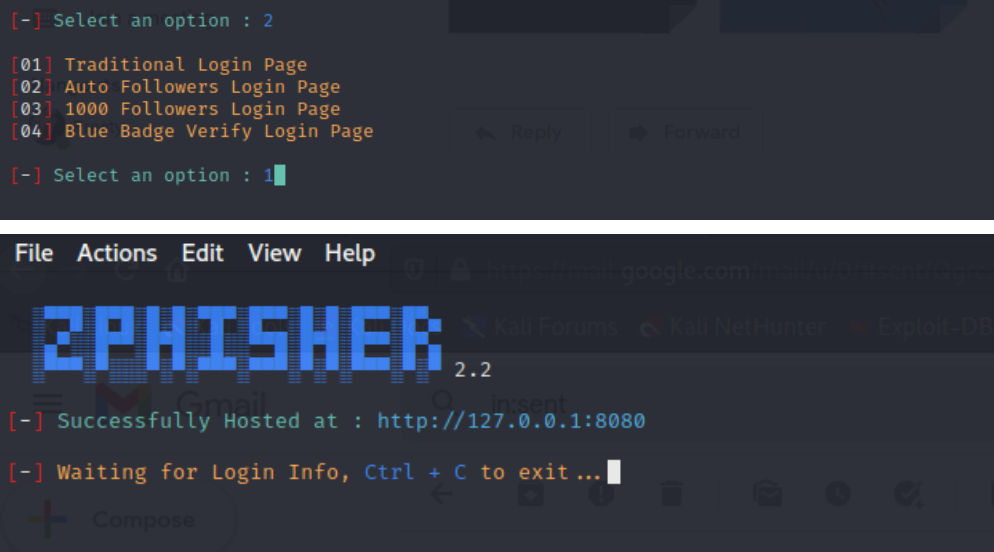
When it starts running, choose a phishing page to use for your scam and the method you want to use to achieve the breach:
Blackeye
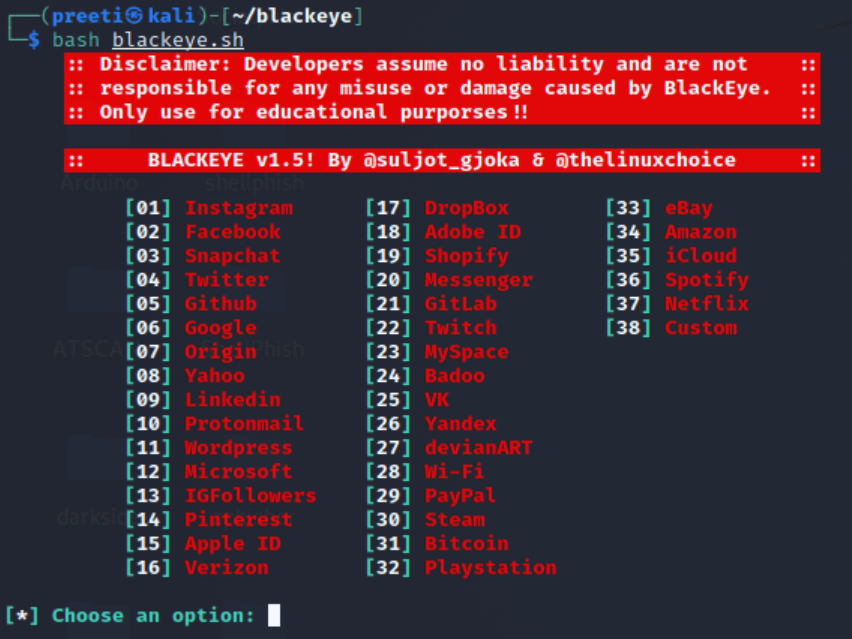
With Blackeye, you can execute attacks efficiently through over thirty templates or create your own customized template if you like.
Install Blackeye and set up the following commands:
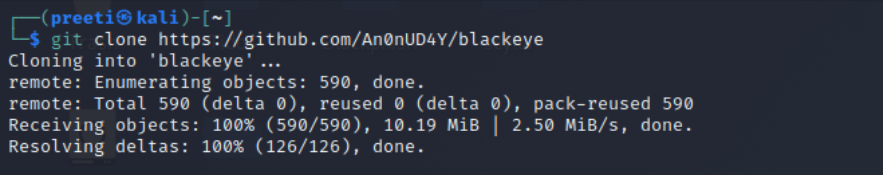
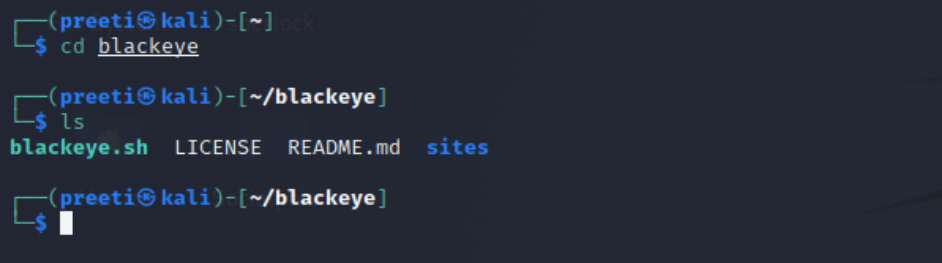
Next, run the tool with “bash blackeye.sh” to launch an attack.
King Phisher
King Phisher allows you to test and promote multiple phishing campaign simulations simultaneously. Flexible and user-friendly, you can use this service for training or simple explanations. You can embed images, create Integrated Sender Policy Framework (SPF) checks, and detect the geolocation of victims.
Install Kingphiser with “mkdir king-phisher,” “cd king-phisher,” “wget-q” and GitHub phishing links. Then, create your phishing pages.
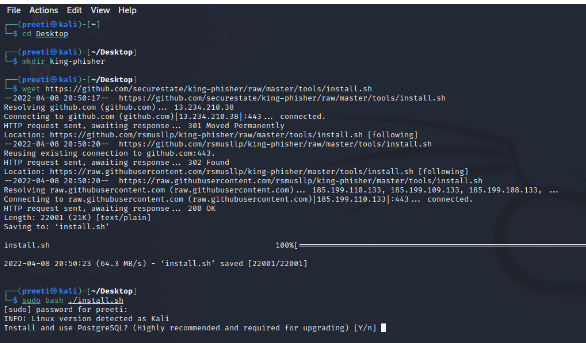
Ghost Phisher
This cloud security audit and attack software can create false access points to which victims connect and input information that hackers hijack. Ghost Phisher has Python Programming Language and Python Qt GUI libraries. You can use penetration tests, credential logging, frequently updated support, and more.
Hidden Eye
Hidden Eye allows users to test keylogging and location-tracking attacks for Kali Linux phishing tools. You can customize most social media, e-commerce, and business pages. Capture the victim's keystrokes, perform live attacks, and create server URL type selection.
Final Thoughts on Kali Linux Open-Source Phishing Training Tools
Whether your organization has five or 500 team members, phishing testing and training are essential to minimizing cyber security vulnerabilities and other data and network security issues. Even if most employees know the characteristics of a phishing attempt, cybercriminals frequently update their methods, so victims need to keep watch.
As you evaluate phishing training tools, consider those that will truly imitate a phishing attack so that you can make the content appear as realistic and believable as possible to the target audience. Remember that people of certain ages and backgrounds may be more or less likely to fall for phishing attempts than others.
Before considering whether to use a tool, spend time using and becoming familiar with it. You can then determine if the tool will meet your goals and expectations. Finally, remember phishing training is not a one-and-done exercise. Making it a regular part of training and preparedness will improve the security posture for the company as well as your workers’ understanding of phishing in general.