Choosing the Right Remote Access Solution for Your Linux Environment

Choosing the right software for your enterprise can be a critical decision to make. With multiple remote access software out on the market, it can be perplexing to narrow down to one solution for your enterprise environment. By considering major business use cases and essential security factors, we have compiled a quick checklist to simplify your decision-making process.
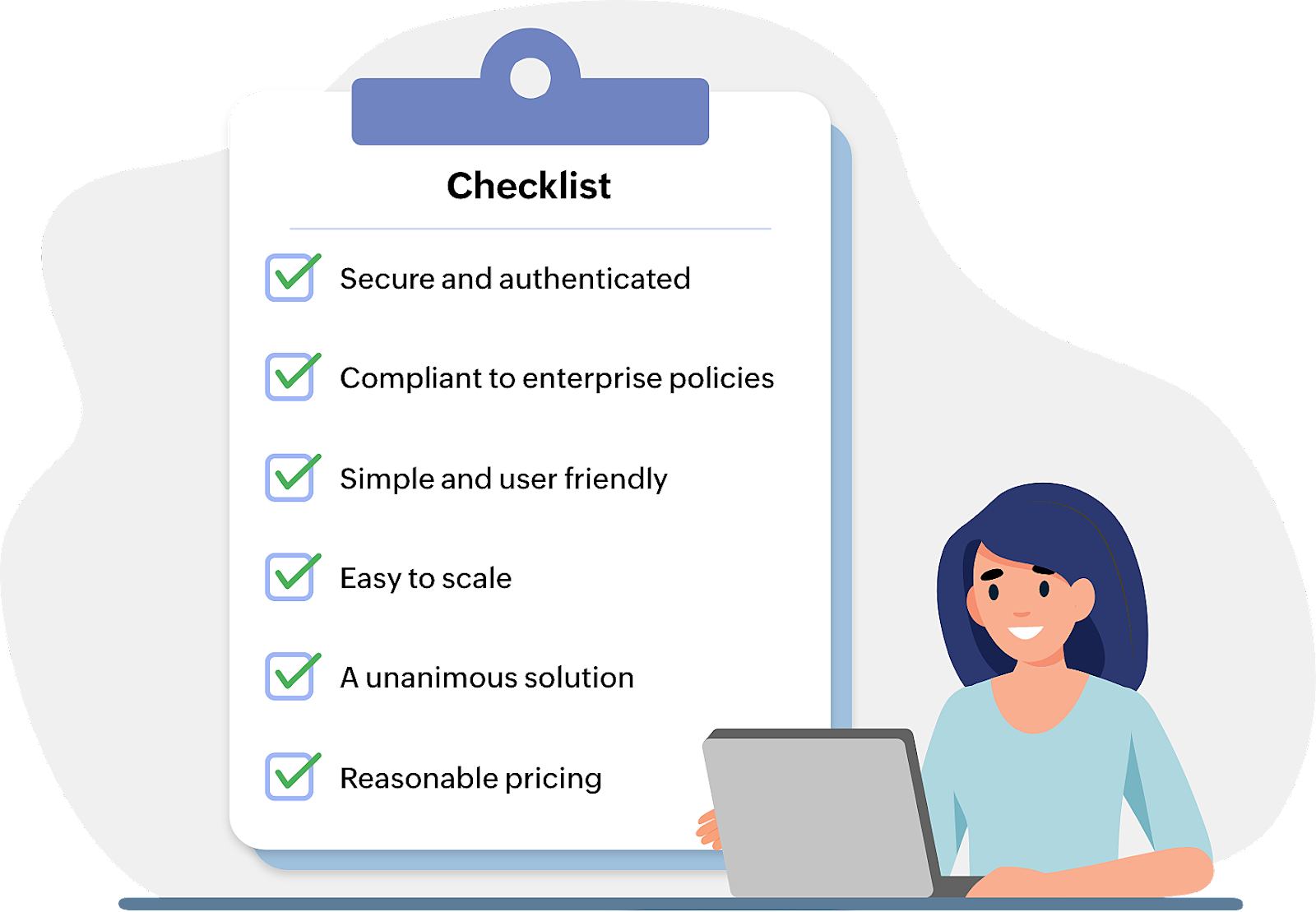
Security
Software without security features and basic authentications will make your enterprise ecosystem vulnerable to threats and hacks. Ensure the software you choose is coupled with robust authentications like SSO, 2FA/MFA, end-to-end encryption, and role-based access, as well as exhaustive recording and reporting features.
Compliance
It is essential organizations adhere to laws and regulations, which is why most of the industry sectors are compliant to mandates and policies like HIPPA, GDPR, and PCI-DSS. When picking a solution, check whether the software will be compliant with these mandates, as well as your specific organizational policies. One thing to look out for is that the software doesn't establish a remote connection without prompting confirmation on the remote device.
Simple to Use
In most scenarios you would want to connect to a remote device instantly. A user-friendly interface and simplified workflow are additional factors you must look into before purchasing the software. Installation and initiating remote sessions must be a seamless process and no additional training should be required.
Scalable & Flexible
Industries and enterprise businesses are growing everyday, resulting in an ever-increasing amount of endpoints that need to be managed. Server and space outages must never be an issue for your organization. The software you choose should be scalable for unlimited endpoints and be available all the time. When it comes to remote access, the major goal is to control a device from anywhere, at any time, even while on the go.
Compatible
Not all devices in your enterprise run Linux OS. There will be a mix of Windows, Mac, and other OSs to consider, so it is essential to ask "will I be able to access a Linux machine from a Windows or Mac device, or vice versa?" If the software lets you access from an Android and iOS device as well, then that's a bonus.
Unlimited & Unbounded
Pricing must not limit the number of remote sessions you are allowed to take. Even from the tip of an iceberg, if you have internet connectivity, you must be able to access your endpoints remotely. A secure remote access solution with communication feature like chat and calls will make your troubleshooting process simple. To make the right business decision for your enterprise, all you need is a boundless and reasonably priced solution.
"If a remote access solution checks each of these, then that's the one you're looking for."
How Remote Access Plus Covers this List!
>Remote Access Plus is a robust remote access and troubleshooting solution for an enterprise ecosystem. It double ticks the checklist by prioritizing security and unifying a solution for various business use cases.
- Exclusive trusted communication between endpoints and servers.
- End-to-end encryption during remote sessions, file transfer etc.
- HIPPA, GDPR, PCI-DSS compliant access from desktops and mobile apps.
- Authenticate with SSO, MFA/2FA, SAML, and more.
- Configure instant notifications for data breaches.
- Provide confined access based on roles.
- Secure servers from vulnerabilities by automating security patches.
- Cloud-based solution to scale up seamlessly.
- Initiate unlimited remote sessions to your endpoints.
- Made user-friendly with a simple web based console.
- Access your Linux computers from Mac, Windows, Android, and iOS devices in a matter of minutes.

It can be confusing to make the right decision when considering different features, various pricing estimations, and perplexing editions provided by vendors. But choosing the right secure remote access solution will simplify your work rather than increasing your burden. So create an exclusive checklist, evaluate multiple solutions and pick out the one that best suits your Linux environment.





















