Linux VPN Myths Exposed: Separating Fact from Fiction for Enhanced Online Security

With concerns regarding online privacy-enhancing technology and overall security on the rise, VPNs have gained immense popularity recently. Nevertheless, an abundance of false information about this network security toolkit has circulated. A Virtual Private Network (VPN) is a tool that enables your computer to establish a secure connection with a distant server, making it seem as if it is physically located in that specific region.
Although businesses commonly employ VPNs to access data on-site, nowadays, the general application of VPNs is for regular individuals to bypass geo-restrictions and enhance their online privacy. To help increase your awareness surrounding this important topic, let's look at some of the most common Linux VPN myths and examine what is actually true.
Myth: Only paranoid Linux users use a VPN.
You may believe a VPN is unnecessary if you reside in a nation without stringent censorship regulations. Nevertheless, the prevalence of hacking, data collection, tracking, and targeted advertising is evident in any country with internet access. Data and cloud security breaches in any country with internet access are frequent, expensive, and endless. Often we connect to public Wi-Fi networks at places like airports or coffee shops without a second thought. However, we must always be sure that these networks are trustworthy and not operated by hackers. Even if a public network appears reliable, as long as it remains unsecured, virtually anyone with IT knowledge can gain access to your browsing activity, personal information, and passwords.
Myth: Linux VPNs are only for experts.
If you need more confidence in your technical abilities, the concept of VPNs and their impact on networking may seem daunting. However, modern VPNs are incredibly user-friendly and straightforward to set up. In most cases, you must download a VPN app, log in to your account, and click a button to connect. You are not required to navigate complex software or anything of that nature. This makes utilizing a VPN so easy to do, allowing you to lessen the number of network security threats you face while out of the house.
Myth: Using a VPN makes me 100% anonymous.
A reliable VPN service can significantly enhance your online privacy and bring you closer to achieving a level of anonymity. By establishing an encrypted tunnel between your device and the desired destination, a VPN allows you to access the internet from a different country. While this connection to a VPN server provides considerable privacy, it would be dishonest to claim that it makes you completely anonymous. Nonetheless, a VPN helps with your data and network security and involves various crucial components that ensure no information passes through the encrypted tunnel.
A VPN undoubtedly enhances privacy, but it is important to note that confidentiality and anonymity are different. While a VPN can assist in maintaining confidentiality, it does not guarantee complete anonymity. Many individuals seek out VPNs to protect their privacy, but your location can still be tracked even while implementing a VPN. Recognizing that every piece of information you share online is stored in a database somewhere is crucial. Moreover, your data has likely been collected and utilized without your knowledge, whether for marketing or surveillance purposes. We are all identifiable on the internet, and our right to privacy is constantly at risk.
Using a VPN and encryption certainly adds an extra layer of difficulty for hackers, making attacks on network security more difficult to achieve. However, individuals with the appropriate skills and tools can still identify their true identity by analyzing their digital footprint while browsing the internet.
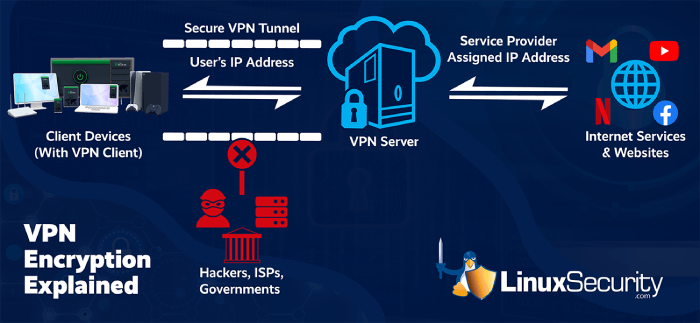
Myth: Using a VPN protects me from all risks online.
While a VPN is a valuable network security toolkit and privacy-enhancing technology, it should not be the universal solution that you use. You must remain cautious while browsing, as even with a VPN enabled, you need to avoid clicking on questionable links since a VPN cannot shield you from network security threats if you willingly provide personal information to scammers. While specific VPNs offer features that conceal suspicious links and protect against phishing attempts, it is still necessary to exercise caution when selecting what to click on. Although a VPN makes it more challenging for individuals to target you, if you choose to trust scammers, VPNs are unable to protect you from their actions.
Additionally, it is essential to acknowledge that a VPN does not serve as a substitute for antivirus software. To combat malware infecting your device, antivirus software remains your best option. Typically, it functions by promptly alerting you through a pop-up message when attempting to visit a hazardous website. Although a VPN is highly effective in preventing hacking attempts and safeguarding your privacy by concealing your IP address, it should not be mistaken for an antivirus solution.
Myth: I don’t need a VPN because I don’t do anything illegal.
It would be unwise to assume that no one utilizes VPNs for illicit activities. However, VPNs serve many purposes beyond merely acquiring copyrighted content or engaging in dubious dealings. Online anonymity proves beneficial when safeguarding oneself on public WiFi and evading data theft, tracking, and surveillance. Additionally, a VPN is essential for bypassing censorship while traveling and accessing banking apps from anywhere and at any time. It is necessary to dispel the misconception that VPNs are illegal, as this notion is far from accurate, and there are lots of companies that use VPNs to maintain data and network security.
The use of VPNs is restricted in countries such as China, Russia, Turkey, and Iraq due to the government's desire to exert control over their citizens' online activities. These countries are particularly opposed to VPNs because they are tools that actively counteract censorship.
Myth: Using a VPN will slow down my Internet connection.
Although a VPN may cause a decrease in internet speed, this is not always the case. When traffic passes through a VPN server, the encryption and decryption process can result in a slower connection. However, this issue is more commonly experienced when connected to remote servers. The optimal connection is achieved when servers that are closer in proximity are used. Therefore, unless there is a specific need to connect to a distant server, choosing nearby cities or neighboring countries is advisable. Interestingly, a VPN can even enhance your connection speed. It is particularly beneficial for internet users in the US and other countries.
VPNs are essential for those who often encounter ISP throttling while engaging in activities such as streaming Netflix, watching YouTube, or performing online tasks demanding high bandwidth. ISPs implement this measure to conserve their network resources, although it may be deemed unfair since users have already paid for their internet service and its associated speed. This is where a VPN comes into play, enhancing your internet connection speed by concealing your online activities from your ISP while maintaining your overall data and network security.
Myth: I can use Tor and Proxies instead of a VPN.
Tor networks and proxies often get mentioned alongside VPNs but should be considered different. While they may appear similar, their functionalities differ significantly when it comes to how the services protect your data and network security. Proxies solely conceal your IP address without encrypting your data, making them less effective than VPNs. It's important to note that free proxy servers can be highly unsafe since their ownership is often unknown. You should also be cautious when utilizing both free proxies or free VPNs. Tor offers a certain level of anonymity to its users, but regular internet users do not typically benefit significantly from this service due to its slow connection speed and poor user experience.
Is Tor a VPN?
While Tor is not classified as a VPN, it offers similar advantages and features. It employs robust encryption to conceal your whereabouts, identity, and online auctions.
However, instead of creating a virtual private network that directs data through an encrypted passage, Tor masks internet traffic through nodes in the Onion overlay network. Despite its sluggish reputation and lack of complete end-to-end encryption like a VPN, Tor enables users to access dark web platforms, including search engines and markets.
Myth: All VPNs are the same.
Navigating the saturated VPN market can be confusing. The primary feature of a VPN is its ability to conceal your IP address and ensure private browsing. This is the key selling point for most VPNs, so they may seem similar. However, not all VPNs offer the same level of encryption or a wide range of server locations. While some VPNs allow up to five simultaneous connections, others, like Surfshark, have no limit.
Also, various VPN providers offer additional features such as ad and malware blocking, connecting to multiple servers simultaneously, and whitelisting capabilities. It is essential to consider these factors when choosing a modern and up-to-date VPN provider to use as a network security toolkit.
Myth: I don’t need to pay for a VPN when I can get one for fre e.
e.
A VPN is a complex network security toolkit designed to safeguard your privacy, requiring resources to ensure its functionality and security. Even free VPN providers need funds to develop their products, so where do they get the money from?
These providers often sell your browsing history, online shopping habits, and other data to the highest bidder to generate income that they use to fund your protection. Although some free VPN developers may have good intentions, it's important to remember that a VPN is still a product that requires funding for its creation and promotion. Instead of risking your online security with a free VPN, invest in an affordable option like Surfshark to protect your company.
Final Thoughts on Linux VPN Usage
It is important to question VPNs prior to using them, as you must understand what types of services you are signing up to receive. However, there are a lot of VPN myths that need to be debunked in order to ease workers who are using VPNs for the first time. Familiarizing yourself with the functions, advantages, and limitations of a VPN is crucial. Hopefully, this article has provided you with a fresh perspective on Linux VPNs and the common misconceptions surrounding them





















