Testing for Password Cracking Attack Risks

Simple passwords can be incredibly weak, whether they match the username, are a blank password, or use keyboard combinations ("qwerty"). These types of passwords may be more accessible to remember, but they do not combat cybercriminals interested in stealing your information and threatening your data and network security. A 2019 Google study showed that seventy-five percent of Americans were frustrated with keeping track of their passwords. This statistic supports the OWASP's SecLists project study that found that the five most common weak passwords are "123456," "Password," "12345678," "qwerty," and "123456789." Therefore, instigating cloud security breaches through brute-force attacks in network security has become the norm for cybercriminals. Weak passwords allow unauthorized access into a server, leading to catastrophic consequences like data loss and long-term downtime. Understanding how to store passwords and prevent attacks is crucial to maintaining data and network security. This article will discuss password cracking and testing tools that sysadmins can implement to improve security posture.
What is Password Cracking?
Password cracking is a hacking technique where cybercriminals obtain passwords through encrypted data stored in a computer or communicated through a server. System administrators can use password-cracking instruments as network security toolkits to see how hackable company passwords are. Then, they can have employees change weak passwords to prevent related cybersecurity vulnerabilities from continuing to be risky. The best tools can handle various targets simultaneously so you can see how effective different protocols and cybersecurity platforms are against a network security threat.
What Types of Password Cracking Attacks Exist?
 There are three common types of password-cracking attacks in network security that businesses must keep in mind while testing their servers for weaknesses that require security patching:
There are three common types of password-cracking attacks in network security that businesses must keep in mind while testing their servers for weaknesses that require security patching:
- Dictionary attack: These cloud security breaches start by collecting a list of previously leaked data that offers words, phrases, and possible passwords that a server uses. A dictionary attack goes through every password and phrase in the list to find the right one and break into the system.
- Brute-force attack: During these attacks in network security, password cracking tools will try to guess every password combination possible within a specific range and criteria that the user specifies. While this process is effective, it also moves quite slowly, as a nine-character password with upper- and lowercase letters and special characters can take up to nine years to crack.
- Rainbow tables: A cybercriminal will compare an existing data dump to a list of password hashes to see if they can determine the correct password in plaintext. Security-oriented applications usually have passwords stored in fixed-length hashes to make it more difficult to hack, so using rainbow tables works through these difficulties much easier and faster than brute-force attacks in network security. However, these cloud security breaches do not work when password hashes have been salted and their salt values are too large, as cracking the password would be a much more complex task.
What Tools Can I Use to Test Password Cracking?
An effective password cracker tool is essential so a business can determine if passwords are a site for cybersecurity vulnerabilities within their company. Here are a few options from which to choose when deciding how to test password cracking on your server.
John the Ripper
Released in 1996, John the Ripper is an open-source native, password cracker tool that was originally produced for UNIX-based systems. Today, the tool can run on many different operating systems including Android, Linux, macOS, and Windows. Designed to test password strength, brute-force encrypted passwords, and crack passwords via dictionary attacks, the tool quickly grew in popularity, and today is one of the most recognizable password cracker tools. Some of its key features include multiple modes to speed up password cracking, automatically detecting the hashing algorithm used by the encrypted passwords and the ease of configuring and running the tool. The tool comes in both GNU-licensed and proprietary versions with the latter being designed for use by professional penetration testers.
John the Ripper Modes and a Use-Case
John the Ripper utilizes modes to best meet the needs of its users. Three modes come with the tool:
- Single crack mode: This mode is recommended to be run first since it is the quickest mode. Single crack mode utilizes information from UNIX passwd files as presented in GECOS fields within UNIX passwd files or shadow files to guess passwords. This is helpful for use cases where a user has to set a password for an account based on commonly available information or a phrase in the username such as root:root or radha:radha456.
- Wordlist mode: Similar in its operation to a dictionary attack, this mode relies on the user providing a text file with a list of passwords, ideally one per line with no duplicates. The application also comes with a set of default wordlists, with the proprietary version offering more choice.
- Incremental mode: An equivalent mode to a brute-force attack method, this mode is only effective for most weak passwords. If a password is long enough or complex enough, this mode may never be able to complete in a decent amount of time and never terminate. In the case of several combinations being too large, the user will have to interrupt this mode.
Here are some examples of use-cases for John the Ripper:
- Cracking a user account password in Kali Linux: This use-case scenario demonstrates the simplicity of using John the Ripper for cracking a user account password on Kali Linux. Say the user creates an account using the command:

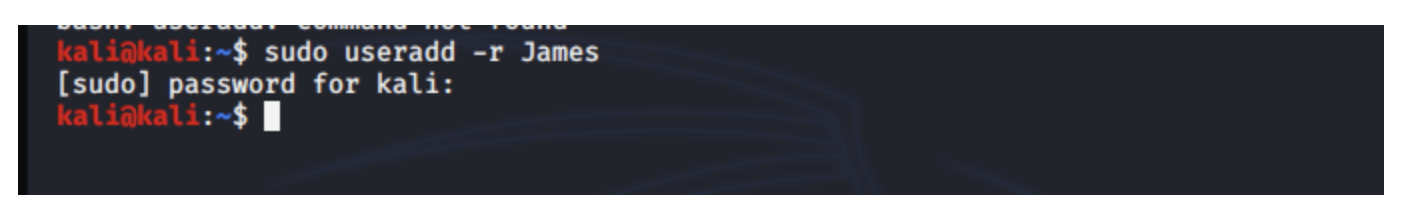
Say the user then sets the password for this account:

To crack the password for the account with the username ‘James’ run the following command:

Not only will John the Ripper identify the hash method and display it on the terminal, but it will also decode the password hash into a raw password and display this password as well.
Hashcat
Hashcat is a popular and effective open-source password cracking tool widely used by penetration testers and system administrators. Considered the world’s first and only in-kernel engine, Hashcat supports many different platforms and operating systems such as Linux, macOS, and Windows for desktops. The tool also has mobile support for Android, iOS, and Windows as well. However, an issue with Hashcat is that it’s limited in the kinds of passwords that can be recovered since, unlike John the Ripper which can recover passwords for databases and operating systems, this tool is mostly limited to documents such as PDF files, and WIFI passwords. Still, Hashcat is very much an effective password cracker tool to consider.
Hashcat’s Attack Arsenal and Use-Case
At the most basic level Hashcat can guess a password, hash it, and then compare the resulting hash to the one it’s trying to crack. In addition to these brute-force attempts, Hashcat also supports dictionary attacks, combinator attacks, mask attacks, and rule-based attacks.
- Dictionary attack: Hashcat can utilize a word list text file to perform a dictionary attack. Users can start with the word list rockyou.txt. Containing more than 14 million passwords sorted by the frequency of use, using the word list with Hashcat can make for a very effective password cracker test.
- Combinator attack: These kinds of attacks work best for passwords that are two words together without a space. For example, passwords such as ‘yellowcar’ or ‘blackbike’ count as passwords that are vulnerable to a combinator attack. Hashcat’s way of doing a combinator attack is by taking a dictionary list and creating a new word list of every word combined with every other word. Hashcat can also add punctuation such as hyphens, exclamation points, and other special characters to create a final word list with passwords such as ‘yellow-car!’ and ‘black-bike!’.
- Mask attack: A mask attack works by looking for passwords with a similar outline. For instance, passwords with one upper case letter followed by six letters and a digit at the end are common for older passwords. Hashcat can search for similar passwords using a mask attack. Mask attacks are often orders of magnitude faster than a brute-force attack, with some brute-force attacks taking 4 years to crack a password compared to 40 minutes for mask attacks.
- Rule-based attack: Hashcat offers a programming language-like syntax for rule-based attacks in which users can specify what kind of passwords to try. This is useful for cases where a user has a sense of how their target constructs a password. One of the most complicated of all the attacks offered by Hashcat, the rule-based attack offers functions to modify, cut or extend words and has conditional operators, making it the most flexible, accurate, and efficient kind of attack.
Here is an example of a use-case for Hashcat:
- Word-list attack on a list of passwords stored in a hash file: A user has two files for the word-list and hash digest. The digest is a bcrypt-md5 hash
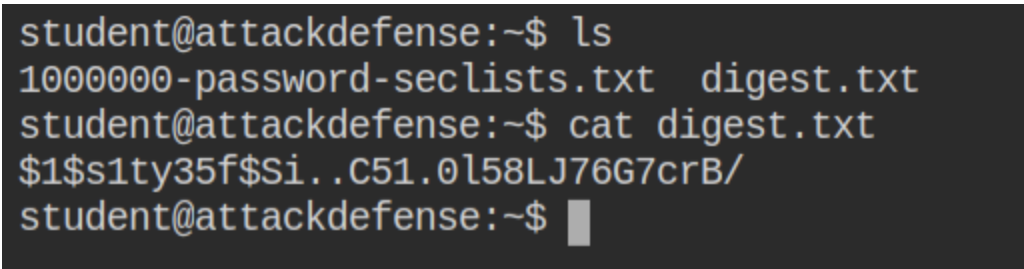
Since Hashcat does not support the name of the hash, the user needs to provide the numeric id of it while launching the attack. These values can be found from hashcat help or the example page on AttackDefense.
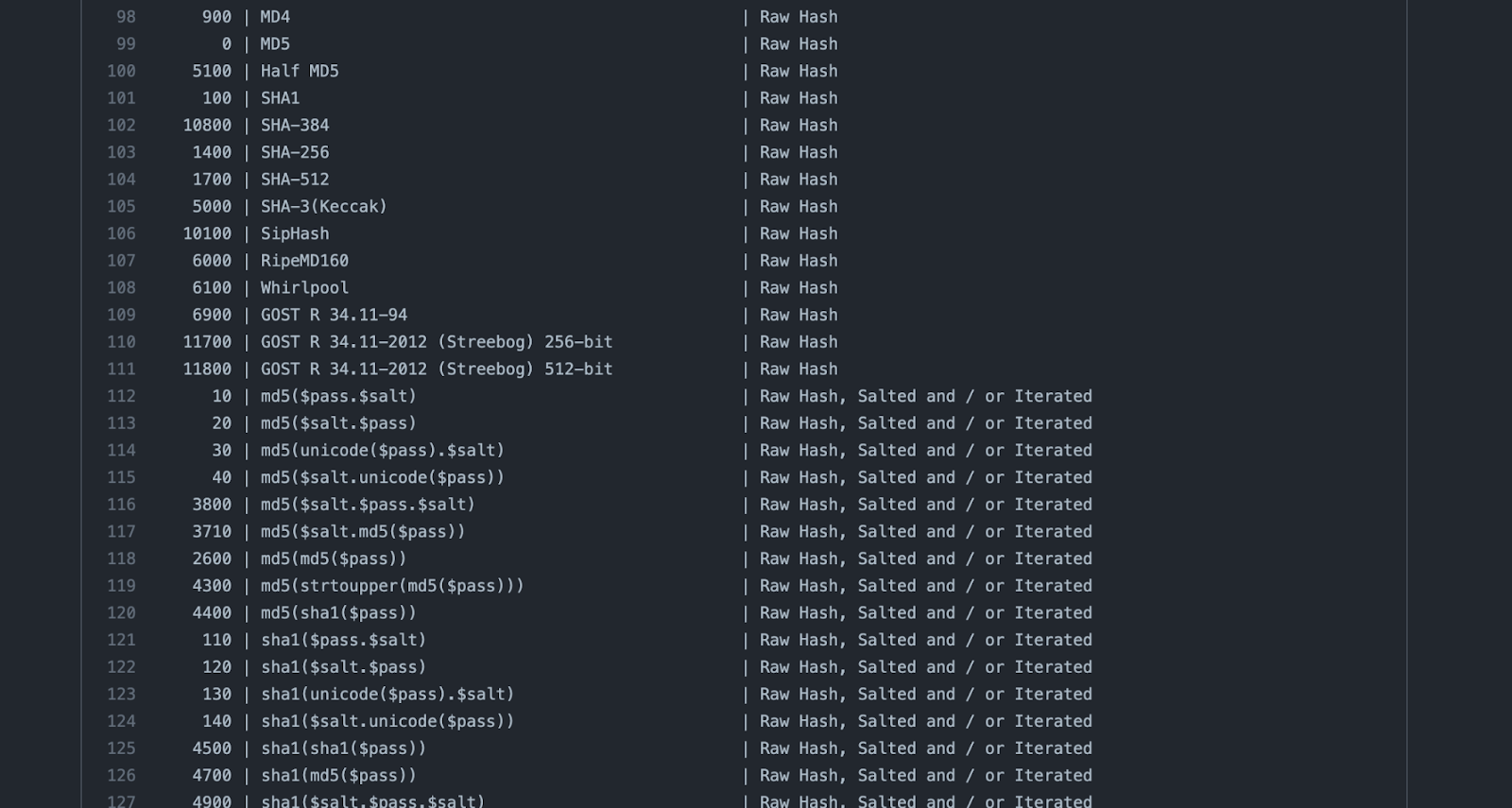
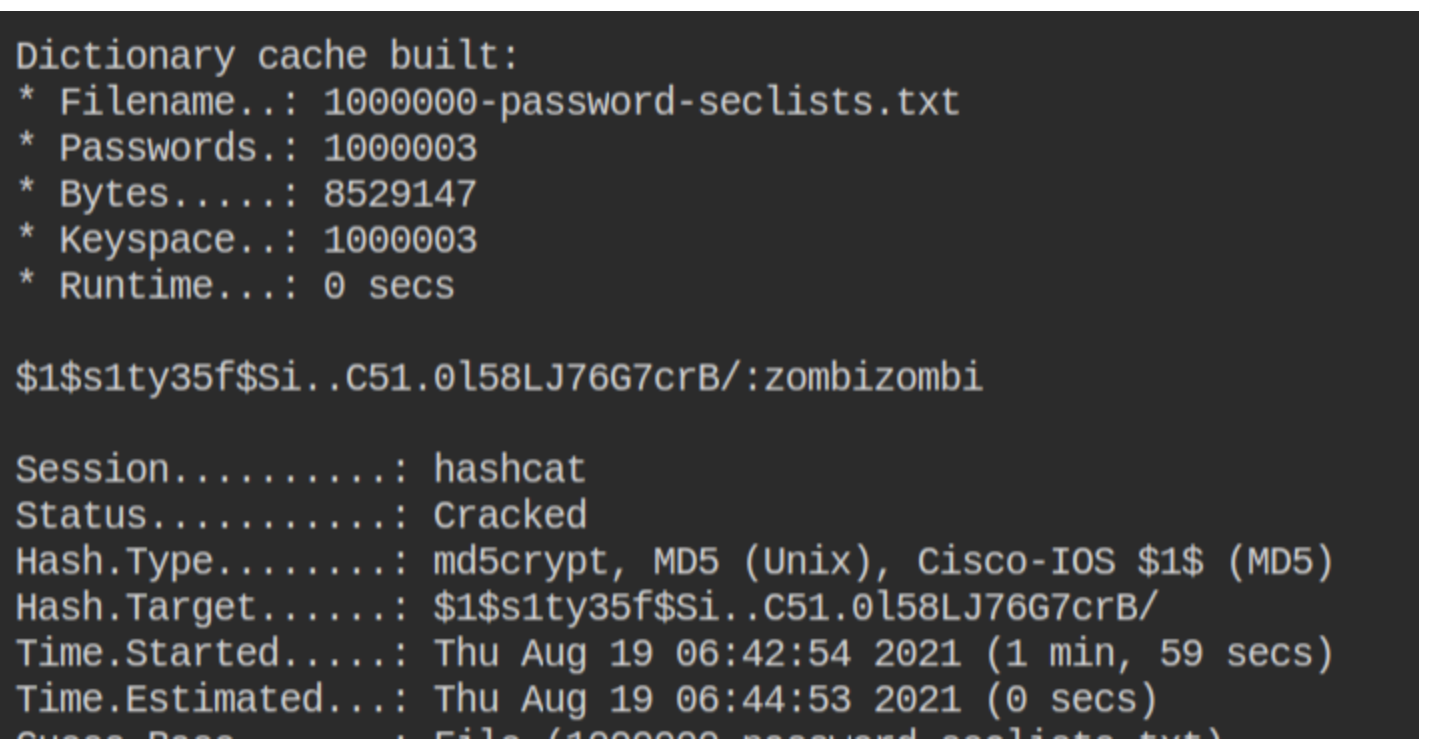
Now that the user has everything required for cracking the password, they can launch the brute-force attack by executing the following command:

Once the kernel is initialized and the comparison starts, the password will be broken and given to the user in the format HASH:PlainText
CrackStation
What differentiates CrackStation from John the Ripper and Hashcat is that CrackStation does not offer a standalone program to be installed on the computer. Instead, the tool is a free web-based password cracker that uses the dictionary attack technique to crack hashes. This allows the program to be used on any kind of operating system, desktop and mobile included. The program also supports multiple protocols, such as LM, md2, md4, md5, ,d5(md5_hex), md5-half, MySQL 4.1+ (sha1(sha1_bin)). NTLM, sha1, sha224, sha256, sha384, sha512, ripeMD160, whirlpool,), and QubesV3.1BackupDefaults. The only downside to CrackStation is that only non-salted hashes without random strings can be used.
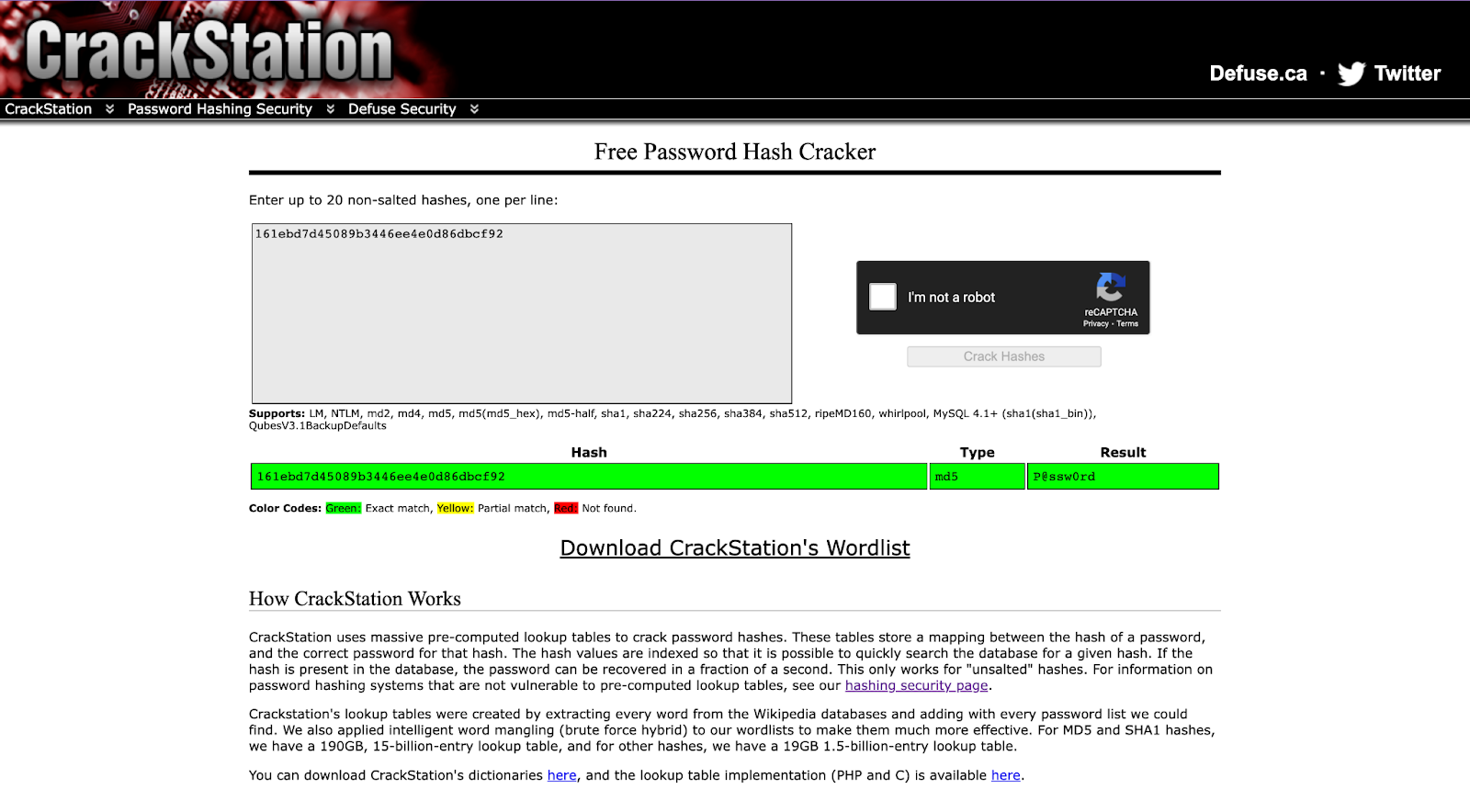
How Does Crackstation Work and What is a Use-Case?
Crackstation uses large pre-computed look-up tables to crack password hashes. These tables can store a mapping between the hash of a password, and the correct password for that hash. What makes it possible to quickly search the database for a given hash is that CrackStation indexes the hash values. If the hash is within the database, the password can be recovered in less than a second. However, this can only work for non-salted hashes. CrackStation offers a hashing security page to check password hashing systems that are not vulnerable to pre-computed look-up tables.
Here is an example of a use-case for CrackStation:
- Cracking MD5 hashes: One of the most simple use-cases for CrackStation, the MD5 hash of a password can easily be translated to syntax using CrackStation. Let’s say for the password ‘P@ssw0rd’ the corresponding MD5 hash is. Plugging in this MD5 hash into CrackStation, the tool returns ‘P@ssw0rd’.
Final Thoughts on Password Cracking
Password-cracking tests are essential to network security toolkits so sysadmins know how to create strong passwords that prevent issues in the future. Sysadmins should implement security measures that safeguard passwords appropriately and keep all information in secure locations. Consider changing passwords every ninety days and creating specifications for passwords so domain administrators can be sure that passwords are secure. Ensure employees understand not to include passwords or login credentials through electronic communications, whether through email or text message, to prevent a cybercriminal from accessing such details during cloud security breaches.
Storing passwords safely is crucial for mitigating password cracking attacks in network security before they occur. Use trustworthy password managers so you can oversee and create complex, unique passwords and create new ones that protect and improve security posture.


















