What You Need to Know About Linux Rootkits

Rootkits are an effective way for attackers to hide their tracks and keep access to the machines over which they have gained control. Read on to learn about rootkits, how to detect them and how to prevent them from being installed on your system in the first place.
What is a Rootkit?
A rootkit is a group of software tools used by an attacker to cover his or her tracks. Rootkits can also contain software which allows the attacker to obtain root access and steal or remove files on a system. This works by using a vulnerable program to obtain root privileges as a regular user, called privilege escalation. This occurs by tricking this vulnerable application, or a person using the vulnerable application, to do something it shouldn’t, ultimately resulting in root privileges.
One of main goals of the threat actor is often to maintain access to a hijacked computer - and rootkits can be very helpful in doing this. Rootkits can also be leveraged to steal sensitive information on a compromised computer or to conceal other malware. In some cases, rootkits are used to turn a hijacked computer into a “Zombie” computer, which can be used to launch attacks on other systems and operate botnets.
Modern rootkits are typically bundled with payloads, and are used to hide these payloads. Because the payloads that accompany these rootkits are malicious, the majority of modern rootkits are classified as malware.
Rootkits can either be installed on a system automatically, or by an attacker who has obtained root (or Administrative) access to a system. Root access can be gained through a direct attack on the system, the exploitation of a known vulnerability or a password that has been obtained using tactics such as cracking or phishing. In certain instances, rootkits are intentionally installed by an authorized user for purposes such as enforcing digital rights management (DRM), detecting threats - for instance, in a honeypot or honeynet - or enhancing security or emulation software.
Good rootkits are very difficult to detect and remove - they can be running on one's computer without his or her knowledge for an extended period of time. For instance,Intezer security researchers identified an undetected Linux rootkit which hid SSH connections by hooking fopen on /dev/net/tcp and concealed itself via hooking readdir. At the time of discovery, the threat was undetected by all engines in VirusTotal.
In fact, one of the hashes was referenced in the discovery of the coinminer Kinsing botnet attack, where attackers exploited vulnerabilities in the popular SaltStack infrastructure automation software to infect cloud servers.
We spoke with Ari Eitan, VP of Research at the malware analysis company Intezer, who explains: "The Linux threat ecosystem is heavily concentrated with financial driven crypto-miners and DDoS botnet tools which primarily target vulnerable servers. Recently, we have seen an increase in sophisticated threats such as rootkits, which are a very effective way for attackers to hide their tracks on a victim’s machine.”
Rootkits are written for many different operating systems; however, this article will solely examine Linux rootkits.
A Brief History of Linux Rootkits
The first rootkits were maliciously modified administrative toolsets for Unix-like operating systems such as Linux that granted attackers administrative access. These “first-generation” rootkits were fairly easy to detect using tools such as Tripwire that had not been compromised to access the same information.
The first known rootkit was written in 1990 for Sun Microsystems’ Sun OS Unix operating system. Since then, rootkits and the uses for them have evolved significantly and become much harder to detect.
In one notorious 2005 rootkit scandal that helped raise awareness of rootkits among the general public, Sony BMG published CDs with copy protection and digital rights management software. The software installed a rootkit which limited the user’s ability to access the CD. Sony BMG released patches to uninstall the rootkit, but these patches exposed users to an even more serious security vulnerability. A class-action lawsuit against Sony BMB ensued and the company eventually recalled the CDs.
Types of Linux Rootkits
User-Mode Rootkits
The simplest type of rootkit and the easiest type to detect and remove operates at the user level. These rootkits can replace a user application with a modified program of their own. They are fairly easy to detect because one can trust the kernel of the operating system. User-mode rootkits can be injected through a variety of different mechanisms including the use of vendor-supplied application extensions, the interception of messages, debuggers, the exploitation of security bugs or API patching.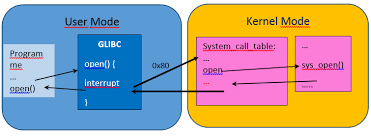
Kernel-Mode Rootkits
Another type of rootkit operates at the kernel level. These rootkits are harder to find and remove because one can't fully trust the kernel on which the rootkit has been installed. Malicious hackers have the ability to delete logs and replace system calls in order to hide their tracks. This type of rootkit is usually installed as a Linux Kernel Module (LKM). Some common kernel-mode rootkit variants include bootkits - or rootkits that can infect startup code like the Master Boot Record, firmware and hardware.
Here is a tutorial that explains how to write a very simple LKM that will allow you to get instant root on whichever machine it is installed on. Modules like this one can be used to masquerade the actions of a threat actor.
Here is a list of awesome user-mode and kernel-mode rootkits - mainly for older kernels - you’ll want to check out.
What Are Some Common Linux Rootkit Techniques?
Using the Linux Kernel Module, a rootkit can modify the kernel's syscall table. By doing this, the rootkit can replace a system call to point to a program of its own.
Another technique that a rootkit can use is to delete a log entry on a system so there will be no log entry of the attackers’ activities. Also, to hide the threat actor’s tracks, the rootkit can replace standard Unix programs such as ps in order not to show the processes that the rootkit is running.
Detecting & Removing Linux Rootkits
The main challenge in detecting well-designed rootkits is that users can't trust the kernel and operating system on which the rootkit is installed. This makes it difficult to identify rootkits by installing detection software directly on the affected operating system. 
An experienced administrator can attempt to identify a rootkit by installing a packet sniffer on an unaffected machine on the same network to analyze the information being sent to and from the machine which may have a rootkit installed on it. Looking at the local log files, or any other files on the system, will not always allow the system administrator to detect an attacker using a rootkit because the rootkit can delete the entries that the attacker makes, or modify the files on the system that would be used to display that information.
Another method of detecting rootkits is to boot from a live CD. This allows a user to trust the kernel and the software running on the Linux CD in order to investigate the files on the possibly-affected computer for rootkits. Also, there are tools and programs available for Linux that search for rootkits locally; however, these programs depend on the local ps command to find them, which an attacker can change to whatever he or she chooses by using a rootkit. Another problem with this approach is that the rootkit can detect and change the security software on the compromised system.
Some tools and programs available for identifying rootkits and other types of Linux malware include:
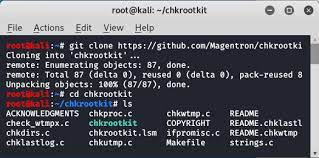 Chkrootkit and rkhunter are tools that scan local systems, identifying any potentially malicious software such as malware and viruses that masks its existence on a system.
Chkrootkit and rkhunter are tools that scan local systems, identifying any potentially malicious software such as malware and viruses that masks its existence on a system.- Lynis is a command-line application that scans a local or remote system to help an auditor identify potential security issues.
- Linux Malware Detect (LMD) is a malware scanner that can be used to detect malware in shared Linux environments. It utilizes threat data from network edge intrusion detection systems to identify and extract malware that is actively being used in attacks and generates signatures for detection. This tool also derives threat data from user submissions and community resources. Rootkits are designed to be very difficult to detect and remove. If a user finds a rootkit on his or her system, it can be extremely difficult to ensure that it has been removed. The only way to know that a rootkit is fully removed from a compromised system is to completely reinstall the system from a trusted source. If you suspect that your system has been compromised, the entire system should be reinstalled from trusted media. The integrity of any data on the system should be thoroughly investigated prior to being restored.
Linux Rootkit Prevention & System Monitoring
The only surefire way to prevent a rootkit is to minimize the opportunities an attacker has to gain access to your system and install an exploit. In order to install a rootkit, malicious actors must gain administrative access to the system they are targeting in some way - whether it be by tricking a user into granting them root access or by compromising the system using a security vulnerability. For example, threat actors may compromise a web server, overwrite a system file with their own malicious file or use a system program in a way in which it wasn't intended to be used in order to gain administrative access to a system and install a rootkit.
As you now understand, system hardening is critical in preventing the installation of rootkits on your system. Users should always engage in good security behaviors including applying security patches, implementing the principle of least privilege, installing antivirus software like ClamAV, reducing the attack surface on their system and preferably using SELinux. Engaging in security best practices that are effective in defending against all types of malware such as checking permissions, enabling firewalls, ensuring that remote access portals are properly secured, monitoring network activity, enabling multi-factor authentication (MFA), reviewing system logs regularly and implementing a proactive, multi-layered email security solution will also help protect against rootkits.
Finally, you can monitor your system using a technique called file integrity to detect rootkits quickly by scanning the system for changes. The idea is to make a fingerprint of the machine right after a fresh install and after each newly installed program. A fingerprint is a cryptographic hash function which makes a hash that is dependent upon each bit of data in a file. After this hash is made, by calculating and comparing the stored hash value with the current hash value, changes in data can be detected.
Using SELinux to Prevent Linux Rootkits
Implementing Security-Enhanced Linux - often referred to as SELinux - is a great way to increase the control you have over access to your system, helping to prevent rootkits and other types of malware from being installed by a malicious actor who has gained administrative access to your system. SELinux is a highly fine-grained mandatory access control (MAC) system that is capable of restricting access to resources on the system beyond what traditional discretionary access control (DAC) methods such as file permissions or access control lists (ACLs) can achieve. For example, there is no reason that a web browser should require access to an SSH key, so in SELinux this information simply wouldn’t be provided to the web browser.
SELinux has now been adopted by various Linux distributions including Fedora, Debian and Ubuntu. Despite the fact that SELinux is very technical and can be difficult to use, the increasingly popular security architecture offers significant benefits for system administrators and users willing to endure the learning curve.
Conclusion
Rootkits are an effective way for attackers to hide their tracks and maintain access to the machines they have gained control of. Well-designed rootkits are very difficult to detect and remove, and can be running on a computer without the user’s knowledge for a long period of time. However, implementing a defense-in-depth security strategy that includes some of the tools and solutions introduced and the best practices covered in this article can mitigate your risk of rootkits or other types of Linux malware being installed on your system.
Have additional questions about rootkits? Connect with us on Twitter - we are happy to help!



















